"
+ }
+ $licensedUserTable = "{0}{1}{2}" -f $licensedUsersTableTop, $licensedUserString, $licensedUsersTableBottom
+
+
+ }
+
+
+ $hash = [ordered]@{
+ TenantName = $companyInfo.displayname
+ PartnerTenantName = $customer.name
+ Domains = $customerDomains.name
+ TenantId = $customer.TenantId
+ InitialDomain = $initialDomain.name
+ Licenses = $licenseTable
+ LicensedUsers = $licensedUserTable
+ }
+ $object = New-Object psobject -Property $hash
+ $365domains += $object
+
+}
+
+# Get all organisations
+#$orgs = GetAllITGItems -Resource organizations
+
+# Get all Contacts
+$itgcontacts = GetAllITGItems -Resource contacts
+
+$itgEmailRecords = @()
+foreach ($contact in $itgcontacts) {
+ foreach ($email in $contact.attributes."contact-emails") {
+ $hash = @{
+ Domain = ($email.value -split "@")[1]
+ OrganizationID = $contact.attributes.'organization-id'
+ }
+ $object = New-Object psobject -Property $hash
+ $itgEmailRecords += $object
+ }
+}
+
+$allMatches = @()
+foreach ($365tenant in $365domains) {
+ foreach ($domain in $365tenant.Domains) {
+ $itgContactMatches = $itgEmailRecords | Where-Object {$_.domain -contains $domain}
+ foreach ($match in $itgContactMatches) {
+ $hash = [ordered]@{
+ Key = "$($365tenant.TenantId)-$($match.OrganizationID)"
+ TenantName = $365tenant.TenantName
+ Domains = ($365tenant.domains -join ", ")
+ TenantId = $365tenant.TenantId
+ InitialDomain = $365tenant.InitialDomain
+ OrganizationID = $match.OrganizationID
+ Licenses = $365tenant.Licenses
+ LicensedUsers = $365tenant.LicensedUsers
+ }
+ $object = New-Object psobject -Property $hash
+ $allMatches += $object
+ }
+ }
+}
+
+$uniqueMatches = $allMatches | Sort-Object key -Unique
+
+foreach ($match in $uniqueMatches) {
+ $existingAssets = @()
+ $existingAssets += GetAllITGItems -Resource "flexible_assets?filter[organization_id]=$($match.OrganizationID)&filter[flexible_asset_type_id]=$assetTypeID"
+ $matchingAsset = $existingAssets | Where-Object {$_.attributes.traits.'tenant-id' -contains $match.TenantId}
+
+ if ($matchingAsset) {
+ Write-Host "Updating Office 365 tenant for $($match.tenantName)"
+ $UpdatedBody = Build365TenantAsset -tenantInfo $match
+ $updatedItem = UpdateITGItem -resource flexible_assets -existingItem $matchingAsset -newBody $UpdatedBody
+ }
+ else {
+ Write-Host "Creating Office 365 tenant for $($match.tenantName)"
+ $newBody = Build365TenantAsset -tenantInfo $match
+ $newItem = CreateITGItem -resource flexible_assets -body $newBody
+ }
+}
\ No newline at end of file
diff --git a/Office365UserActivityAndUsage/CreateApp.ps1 b/Office365UserActivityAndUsage/CreateApp.ps1
new file mode 100644
index 0000000..e3cdf60
--- /dev/null
+++ b/Office365UserActivityAndUsage/CreateApp.ps1
@@ -0,0 +1,222 @@
+# This script needs to be run by an admin account in your Office 365 tenant
+# This script will create an Azure AD app in your organisation with permission
+# to access resources in yours and your customers' tenants.
+# It will export information about the application to a CSV located at C:\temp\.
+# The CSV will include the Client ID and Secret of the application, so keep it safe.
+
+# Confirm C:\temp exists
+$temp = Test-Path -Path C:\temp
+if ($temp) {
+ #Write-Host "Path exists"
+}
+else {
+ Write-Host "Creating Temp folder"
+ New-Item -Path C:\temp -ItemType directory
+}
+
+$applicationName = "GCITS User Activity Report Reader"
+
+# Change this to true if you would like to overwrite any existing applications with matching names.
+$removeExistingAppWithSameName = $false
+# Modify the homePage, appIdURI and logoutURI values to whatever valid URI you like.
+# They don't need to be actual addresses, so feel free to make something up (as long as it's on a verified domain in your Office 365 environment eg. https://anything.yourdomain.com).
+$homePage = "https://secure.gcits.com"
+$appIdURI = "https://secure.gcits.com/$((New-Guid).ToString())"
+$logoutURI = "https://portal.office.com"
+
+$URIForApplicationPermissionCall = "https://graph.microsoft.com/beta/reports/getMailboxUsageDetail(period='D7')?`$format=application/json"
+$ApplicationPermissions = "Reports.Read.All Directory.Read.All Sites.Manage.All"
+
+Function Add-ResourcePermission($requiredAccess, $exposedPermissions, $requiredAccesses, $permissionType) {
+ foreach ($permission in $requiredAccesses.Trim().Split(" ")) {
+ $reqPermission = $null
+ $reqPermission = $exposedPermissions | Where-Object {$_.Value -contains $permission}
+ Write-Host "Collected information for $($reqPermission.Value) of type $permissionType" -ForegroundColor Green
+ $resourceAccess = New-Object Microsoft.Open.AzureAD.Model.ResourceAccess
+ $resourceAccess.Type = $permissionType
+ $resourceAccess.Id = $reqPermission.Id
+ $requiredAccess.ResourceAccess.Add($resourceAccess)
+ }
+}
+
+Function Get-RequiredPermissions($requiredDelegatedPermissions, $requiredApplicationPermissions, $reqsp) {
+ $sp = $reqsp
+ $appid = $sp.AppId
+ $requiredAccess = New-Object Microsoft.Open.AzureAD.Model.RequiredResourceAccess
+ $requiredAccess.ResourceAppId = $appid
+ $requiredAccess.ResourceAccess = New-Object System.Collections.Generic.List[Microsoft.Open.AzureAD.Model.ResourceAccess]
+ if ($requiredDelegatedPermissions) {
+ Add-ResourcePermission $requiredAccess -exposedPermissions $sp.Oauth2Permissions -requiredAccesses $requiredDelegatedPermissions -permissionType "Scope"
+ }
+ if ($requiredApplicationPermissions) {
+ Add-ResourcePermission $requiredAccess -exposedPermissions $sp.AppRoles -requiredAccesses $requiredApplicationPermissions -permissionType "Role"
+ }
+ return $requiredAccess
+}
+Function New-AppKey ($fromDate, $durationInYears, $pw) {
+ $endDate = $fromDate.AddYears($durationInYears)
+ $keyId = (New-Guid).ToString()
+ $key = New-Object Microsoft.Open.AzureAD.Model.PasswordCredential($null, $endDate, $keyId, $fromDate, $pw)
+ return $key
+}
+
+Function Test-AppKey($fromDate, $durationInYears, $pw) {
+
+ $testKey = New-AppKey -fromDate $fromDate -durationInYears $durationInYears -pw $pw
+ while ($testKey.Value -match "\+" -or $testKey.Value -match "/") {
+ Write-Host "Secret contains + or / and may not authenticate correctly. Regenerating..." -ForegroundColor Yellow
+ $pw = Initialize-AppKey
+ $testKey = New-AppKey -fromDate $fromDate -durationInYears $durationInYears -pw $pw
+ }
+ Write-Host "Secret doesn't contain + or /. Continuing..." -ForegroundColor Green
+ $key = $testKey
+
+ return $key
+}
+
+Function Initialize-AppKey {
+ $aesManaged = New-Object "System.Security.Cryptography.AesManaged"
+ $aesManaged.Mode = [System.Security.Cryptography.CipherMode]::CBC
+ $aesManaged.Padding = [System.Security.Cryptography.PaddingMode]::Zeros
+ $aesManaged.BlockSize = 128
+ $aesManaged.KeySize = 256
+ $aesManaged.GenerateKey()
+ return [System.Convert]::ToBase64String($aesManaged.Key)
+}
+function Confirm-MicrosoftGraphServicePrincipal {
+ $graphsp = Get-AzureADServicePrincipal -SearchString "Microsoft Graph"
+ if (!$graphsp) {
+ $graphsp = Get-AzureADServicePrincipal -SearchString "Microsoft.Azure.AgregatorService"
+ }
+ if (!$graphsp) {
+ Login-AzureRmAccount -Credential $credentials
+ New-AzureRmADServicePrincipal -ApplicationId "00000003-0000-0000-c000-000000000000"
+ $graphsp = Get-AzureADServicePrincipal -SearchString "Microsoft Graph"
+ }
+ return $graphsp
+}
+Write-Host "Connecting to Azure AD. The login window may appear behind Visual Studio Code."
+Connect-AzureAD
+
+Write-Host "Creating application in tenant: $((Get-AzureADTenantDetail).displayName)"
+
+# Check for the Microsoft Graph Service Principal. If it doesn't exist already, create it.
+$graphsp = Confirm-MicrosoftGraphServicePrincipal
+
+$existingapp = $null
+$existingapp = get-azureadapplication -SearchString $applicationName
+if ($existingapp -and $removeExistingAppWithSameName) {
+ Remove-Azureadapplication -ObjectId $existingApp.objectId
+}
+
+# RSPS
+$rsps = @()
+if ($graphsp) {
+ $rsps += $graphsp
+ $tenant_id = (Get-AzureADTenantDetail).ObjectId
+ $tenantName = (Get-AzureADTenantDetail).DisplayName
+
+ # Add Required Resources Access (Microsoft Graph)
+ $requiredResourcesAccess = New-Object System.Collections.Generic.List[Microsoft.Open.AzureAD.Model.RequiredResourceAccess]
+ $microsoftGraphRequiredPermissions = Get-RequiredPermissions -reqsp $graphsp -requiredApplicationPermissions $ApplicationPermissions -requiredDelegatedPermissions $DelegatedPermissions
+ $requiredResourcesAccess.Add($microsoftGraphRequiredPermissions)
+
+ # Get an application key
+ $pw = Initialize-AppKey
+ $fromDate = [System.DateTime]::Now
+ $appKey = Test-AppKey -fromDate $fromDate -durationInYears 99 -pw $pw
+
+ Write-Host "Creating the AAD application $applicationName" -ForegroundColor Blue
+ $aadApplication = New-AzureADApplication -DisplayName $applicationName `
+ -HomePage $homePage `
+ -ReplyUrls $homePage `
+ -IdentifierUris $appIdURI `
+ -LogoutUrl $logoutURI `
+ -RequiredResourceAccess $requiredResourcesAccess `
+ -PasswordCredentials $appKey `
+ -AvailableToOtherTenants $true
+
+ # Creating the Service Principal for the application
+ $servicePrincipal = New-AzureADServicePrincipal -AppId $aadApplication.AppId
+
+ Write-Host "Assigning Permissions" -ForegroundColor Yellow
+
+ # Assign application permissions to the application
+ foreach ($app in $requiredResourcesAccess) {
+ $reqAppSP = $rsps | Where-Object {$_.appid -contains $app.ResourceAppId}
+ Write-Host "Assigning Application permissions for $($reqAppSP.displayName)" -ForegroundColor DarkYellow
+ foreach ($resource in $app.ResourceAccess) {
+ if ($resource.Type -match "Role") {
+ New-AzureADServiceAppRoleAssignment -ObjectId $serviceprincipal.ObjectId `
+ -PrincipalId $serviceprincipal.ObjectId -ResourceId $reqAppSP.ObjectId -Id $resource.Id
+ }
+ }
+ }
+
+ # This provides the application with access to your customer tenants.
+ $group = Get-AzureADGroup -Filter "displayName eq 'Adminagents'"
+ Add-AzureADGroupMember -ObjectId $group.ObjectId -RefObjectId $servicePrincipal.ObjectId
+
+ Write-Host "App Created" -ForegroundColor Green
+
+ # Define parameters for Microsoft Graph access token retrieval
+ $client_id = $aadApplication.AppId;
+ $client_secret = $appkey.Value
+ $tenant_id = (Get-AzureADTenantDetail).ObjectId
+ $resource = "https://graph.microsoft.com"
+ $authority = "https://login.microsoftonline.com/$tenant_id"
+ $tokenEndpointUri = "$authority/oauth2/token"
+
+ # Get the access token using grant type password for Delegated Permissions or grant type client_credentials for Application Permissions
+
+ $content = "grant_type=client_credentials&client_id=$client_id&client_secret=$client_secret&resource=$resource"
+
+ # Try to execute the API call 6 times
+
+ $Stoploop = $false
+ [int]$Retrycount = "0"
+ do {
+ try {
+ $response = Invoke-RestMethod -Uri $tokenEndpointUri -Body $content -Method Post -UseBasicParsing
+ Write-Host "Retrieved Access Token" -ForegroundColor Green
+ # Assign access token
+ $access_token = $response.access_token
+ $body = $null
+
+ $body = Invoke-RestMethod `
+ -Uri $UriForApplicationPermissionCall `
+ -Headers @{"Authorization" = "Bearer $access_token"} `
+ -ContentType "application/json" `
+ -Method GET `
+
+ Write-Host "Retrieved Graph content" -ForegroundColor Green
+ $Stoploop = $true
+ }
+ catch {
+ if ($Retrycount -gt 5) {
+ Write-Host "Could not get Graph content after 6 retries." -ForegroundColor Red
+ $Stoploop = $true
+ }
+ else {
+ Write-Host "Could not get Graph content. Retrying in 5 seconds..." -ForegroundColor DarkYellow
+ Start-Sleep -Seconds 5
+ $Retrycount ++
+ }
+ }
+ }
+ While ($Stoploop -eq $false)
+
+ $appInfo = [pscustomobject][ordered]@{
+ ApplicationName = $ApplicationName
+ TenantName = $tenantName
+ TenantId = $tenant_id
+ clientId = $client_id
+ clientSecret = $client_secret
+ ApplicationPermissions = $ApplicationPermissions
+ }
+
+ $AppInfo | Export-Csv C:\temp\AzureADApp.csv -Append -NoTypeInformation
+}
+else {
+ Write-Host "Microsoft Graph Service Principal could not be found or created" -ForegroundColor Red
+}
\ No newline at end of file
diff --git a/Office365UserActivityAndUsage/SyncOffice365UserActivityAndUsage.ps1 b/Office365UserActivityAndUsage/SyncOffice365UserActivityAndUsage.ps1
new file mode 100644
index 0000000..1b557e9
--- /dev/null
+++ b/Office365UserActivityAndUsage/SyncOffice365UserActivityAndUsage.ps1
@@ -0,0 +1,745 @@
+# Azure AD App Details
+$client_id = "EnterYourClientIDHere"
+$client_secret = "EnterYourClientSecretHere"
+$ourTenantId = "EnterYourTenantIdHere"
+$ourCompanyName = "EnterYourCompanyNameHere" # eg. GCITS
+$ourDomainName = "EnterYourDefaultDomainHere" # eg. gcits.com
+$ListName = "Office 365 - IT Glue match register"
+$graphBaseUri = "https://graph.microsoft.com/v1.0/"
+$siteid = "root"
+$UserList = "AAD Users"
+
+
+# IT Glue Details
+# EU tenants may need to update this to "https://api.eu.itglue.com"
+$ITGbaseURI = "https://api.itglue.com"
+$ITGkey = "EnterYourITGlueAPIKeyHere"
+$ITGheaders = @{"x-api-key" = $ITGkey }
+$FlexibleAssetName = "Office 365 User Report"
+
+function Get-GCITSAccessToken($appCredential, $tenantId) {
+ $client_id = $appCredential.appID
+ $client_secret = $appCredential.secret
+ $tenant_id = $tenantid
+ $resource = "https://graph.microsoft.com"
+ $authority = "https://login.microsoftonline.com/$tenant_id"
+ $tokenEndpointUri = "$authority/oauth2/token"
+ $content = "grant_type=client_credentials&client_id=$client_id&client_secret=$client_secret&resource=$resource"
+ $response = Invoke-RestMethod -Uri $tokenEndpointUri -Body $content -Method Post -UseBasicParsing
+ $access_token = $response.access_token
+ return $access_token
+}
+
+function Get-GCITSMSGraphResource($Resource) {
+ $graphBaseUri = "https://graph.microsoft.com/beta"
+ $values = @()
+ $result = Invoke-RestMethod -Uri "$graphBaseUri/$resource" -Headers $headers
+ if ($result.value) {
+ $values += $result.value
+ if ($result."@odata.nextLink") {
+ do {
+ $result = Invoke-RestMethod -Uri $result."@odata.nextLink" -Headers $headers
+ $values += $result.value
+ } while ($result."@odata.nextLink")
+ }
+ }
+ else {
+ $values = $result
+ }
+ return $values
+}
+function New-GCITSSharePointColumn($Name, $Type, $Indexed, $lookupListName, $lookupColumnPrimaryName, $lookupColumnName, $longText) {
+ if ($longText) {
+ $column = [ordered]@{
+ name = $Name
+ indexed = $Indexed
+ $Type = @{
+ maxLength = 0
+ allowMultipleLines = $True
+ #appendChangesToExistingText = $False
+ #linesForEditing = 6
+ #textType = "plain"
+ }
+
+ }
+ }
+ else {
+ $column = [ordered]@{
+ name = $Name
+ indexed = $Indexed
+ $Type = @{ }
+ }
+
+ if ($lookupListName -and $type -contains "lookup") {
+ $list = Get-GCITSSharePointList -ListName $lookupListName
+ if ($list) {
+ $column.lookup.listId = $list.id
+ $column.lookup.columnName = $lookupColumnName
+ }
+ }
+ }
+
+ return $column
+}
+function New-GCITSSharePointList ($Name, $ColumnCollection) {
+ $list = @{
+ displayName = $Name
+ columns = $columnCollection
+ } | Convertto-json -Depth 10
+
+ $newList = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method POST -Body $list
+ return $newList
+}
+
+function Remove-GCITSSharePointList ($ListId) {
+ $removeList = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$ListId" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method DELETE
+ return $removeList
+}
+
+function Remove-GCITSSharePointListItem ($ListId, $ItemId) {
+ $removeItem = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$ListId/items/$ItemId" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method DELETE
+ return $removeItem
+}
+
+function New-GCITSSharePointListItem($ItemObject, $ListId) {
+
+ $itemBody = @{
+ fields = $ItemObject
+ } | ConvertTo-Json -Depth 10
+
+ $listItem = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$listId/items" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method Post `
+ -Body $itemBody
+}
+
+function Get-GCITSSharePointListItem($ListId, $ItemId, $Query) {
+
+ if ($ItemId) {
+ $listItem = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items/$ItemId `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = $listItem
+ }
+ elseif ($Query) {
+ $listItems = $null
+ $listItems = Invoke-RestMethod -Uri "$graphBaseUri/sites/$siteid/lists/$listId/items/?expand=fields&`$filter=$Query" `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = @()
+ $value = $listItems.value
+ if ($listitems."@odata.nextLink") {
+ $nextLink = $true
+ }
+ if ($nextLink) {
+ do {
+ $listItems = Invoke-RestMethod -Uri $listitems."@odata.nextLink"`
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value += $listItems.value
+ if (!$listitems."@odata.nextLink") {
+ $nextLink = $false
+ }
+ } until (!$nextLink)
+ }
+ }
+ else {
+ $listItems = $null
+ $listItems = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items?expand=fields `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = @()
+ $value = $listItems.value
+ if ($listitems."@odata.nextLink") {
+ $nextLink = $true
+ }
+ if ($nextLink) {
+ do {
+ $listItems = Invoke-RestMethod -Uri $listitems."@odata.nextLink"`
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value += $listItems.value
+ if (!$listitems."@odata.nextLink") {
+ $nextLink = $false
+ }
+ } until (!$nextLink)
+ }
+ }
+ return $value
+}
+
+function Set-GCITSSharePointListItem($ListId, $ItemId, $ItemObject) {
+ $listItem = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items/$ItemId/fields `
+ -Method Patch -headers $SPHeaders `
+ -ContentType application/json `
+ -Body ($itemObject | ConvertTo-Json)
+ $return = $listItem
+}
+
+function Get-GCITSSharePointList($ListName) {
+ $list = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists?expand=columns&`$filter=displayName eq '$ListName'" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method GET
+ $list = $list.value
+ return $list
+}
+Function Get-GCITSMSGraphReport ($ReportName, $Resource) {
+ $Report = Get-GCITSMSGraphResource -Resource $Resource
+ if ($Report) {
+ $Report | Add-Member ReportName $ReportName -Force
+ }
+ Write-Host "$reportname - $($report.count)"
+ return $Report
+}
+
+function Get-GCITSSpacingTitleCase ($String) {
+ $String = ($String -creplace '([A-Z\W_]|\d+)(?$(Get-GCITSSpacingTitleCase -String $objectproperty): $($object.$($objectProperty))"
+ }
+ }
+ $reportKeyValue = $stringArray -join "
"
+ }
+ elseif ($reportKey.OriginalPropertyName -eq "assignedLicenses") {
+ $stringArray = @()
+ foreach ($license in $reportKeyValue) {
+ $stringArray += ($licenses | Where-Object { $_.skuid -eq $license.skuid }).skupartnumber
+ }
+ $reportKeyValue = $stringArray -join ", "
+ }
+ elseif ($reportKey.OriginalPropertyName -eq "proxyAddresses") {
+ $stringArray = @()
+ foreach ($address in $reportKeyValue) {
+ $stringArray += ($address -split ":")[1]
+ }
+ $reportKeyValue = $stringArray -join ", "
+
+ }
+ else {
+ if (($reportKeyValue[0].psobject.properties.name | Measure-Object).count -gt 0) {
+ $reportKeyValue = "Detected"
+ }
+ else {
+ $reportKeyValue = "None"
+ }
+ }
+
+ }
+ if ($reportKeyValue -and $field) {
+ $userReportTraits | Add-member $field.'name-key' $reportKeyValue -Force
+ }
+ }
+ }
+
+ foreach ($ITGOrg in $ITGOrgToSync) {
+ $FlexibleAssetBody = [pscustomobject]@{
+ data = @{
+ type = "flexible-assets"
+ attributes = [pscustomobject]@{
+ "organization-id" = $ITGOrg.fields.ITGlueOrgId
+ "flexible-asset-type-id" = $flexibleAsset.id
+ traits = $userReportTraits
+ }
+ }
+ }
+
+ $FlexibleAssetItem = $FlexibleAssetBody | ConvertTo-Json -Depth 10
+ try {
+ $existingFlexibleAssetsForUser = $existingFlexibleAssetsForTenant | Where-Object { $_.attributes.traits.id -eq $user.id -and $_.attributes.'organization-id' -eq $ITGOrg.fields.ITGlueOrgId } | Select-Object -First 1
+ if ($existingFlexibleAssetsForUser) {
+ $updateItem = Set-GCITSITGItem -Resource flexible_assets -existingItem $existingFlexibleAssetsForUser -Body $FlexibleAssetItem
+ }
+ else {
+ $newItem = New-GCITSITGItem -resource flexible_assets -body $FlexibleAssetItem
+ }
+ }
+ catch {
+ Write-Host "Error here: $($error[0])"
+ }
+ }
+ }
+ $TenantsToDisable = $ITGOrgsForTenant | where-object { $_.fields.DisableSync }
+ # Remove Office 365 user reports from tenants where sync is disabled in SharePoint List
+ foreach ($tenant in $TenantsToDisable) {
+ $assetsToRemove = $existingFlexibleAssetsForTenant | Where-Object { $_.attributes.'organization-id' -eq $tenant.fields.ITGlueOrgId }
+ if ($assetsToRemove) {
+ foreach ($item in $assetsToRemove) {
+ Write-Host "Removing $($item.attributes.traits.'user-principal-name') from $($tenant.fields.ITGlueOrg)"
+ Remove-GCITSITGItem -Resource flexible_assets -ExistingItem $item
+ }
+ }
+ }
+ }
+ }
+}
+
+<#
+# If you want to clear out all existing assets, just uncomment and run the following script block once you've initialised the variables and functions at the top of the script.
+# You can do this by selecting the code and pressing F8.
+
+$flexibleAsset = Get-GCITSITGItem -Resource "flexible_asset_types?filter[name]=$FlexibleAssetName"
+[array]$existingAssets = Get-GCITSITGItem -Resource "flexible_assets?filter[organization_id]=$($ITGCompany)&filter[flexible_asset_type_id]=$($flexibleasset.id)"
+
+foreach($item in $existingAssets){
+ Write-Host "Removing $($item.attributes.traits.'user-principal-name')"
+ Remove-GCITSITGItem -Resource flexible_assets -ExistingItem $item
+}
+#>
\ No newline at end of file
diff --git a/Office365UserActivityAndUsage/sync-office-365-user-activity-and-usage-with-it-glue.md b/Office365UserActivityAndUsage/sync-office-365-user-activity-and-usage-with-it-glue.md
new file mode 100644
index 0000000..282e999
--- /dev/null
+++ b/Office365UserActivityAndUsage/sync-office-365-user-activity-and-usage-with-it-glue.md
@@ -0,0 +1,1068 @@
+Sync Office 365 User Activity and Usage with IT Glue
+====================================================
+
+
+
+The Microsoft Graph API provides a bunch of useful user activity and usage reports that provide insight into how users are taking advantage of Office 365 services. This guide will demonstrate how to collect and sync that information with a dynamic flexible asset in IT Glue.
+
+The information we’ll be collecting includes:
+
+* Basic user information with licenses and aliases![Office 365 User Report Detail in IT Glue]
+
+ 
+
+* Office 365 app installs for each user
+
+ 
+
+* Email app usage, SharePoint and Microsoft Teams Activity![Office 365 Email App And SharePoint Usage in IT Glue]
+
+ 
+
+* Mailbox usage and activity
+
+ 
+
+* OneDrive usage and activity![Office 365 OneDrive Usage in IT Glue]
+
+ 
+
+* Yammer activity
+
+This guide is designed for Microsoft Partners who have delegated access to customer tenants.
+
+Prerequisites
+-------------
+
+* To run the first script, you’ll need to install the Azure AD PowerShell Module. You can do this by opening PowerShell as an administrator and running:
+
+ `Install-Module AzureAD`
+
+* To authorise the application to access your own and your customers’ tenants, you’ll need to be a Global Administrator.
+
+Solution outline
+----------------
+
+This solution consists of the following:
+
+### Script 1 – Authorise an Azure AD Application to access customers’ reports
+
+Creates an application with access to Mailbox usage reports for your own and customers’ tenants. This one needs to be run as a Global Admin.
+
+### Script 2 – Syncing Tenant to IT Glue Org matches with SharePoint and Office 365 Usage/Activity Reports with IT Glue
+
+Retrieves the usage reports, creates a SharePoint list of suggested matches between Office 365 tenants and IT Glue organisation. Once matches are confirmed, the Office 365 user details are synced with IT Glue. This script can be run as a regular as a scheduled task or Azure Function
+
+Authorise an Azure AD Application to access customers’ reports
+--------------------------------------------------------------
+
+1. Double click the below script to select it.
+2. Copy and paste the script into a new file in Visual Studio Code and save it with a **.ps1** extension
+3. Install the recommended PowerShell module if you haven’t already
+4. Modify the $homePage and $logoutURI values to any valid URI that you like. They don’t need to be actual addresses, so feel free to make something up. Set the $appIDUri variable to a use a valid domain in your tenant. eg. https://yourdomain.com/$((New-Guid).ToString())![Update HomePage and AppIDUri]
+
+ 
+
+5. Press **F5** to run the script
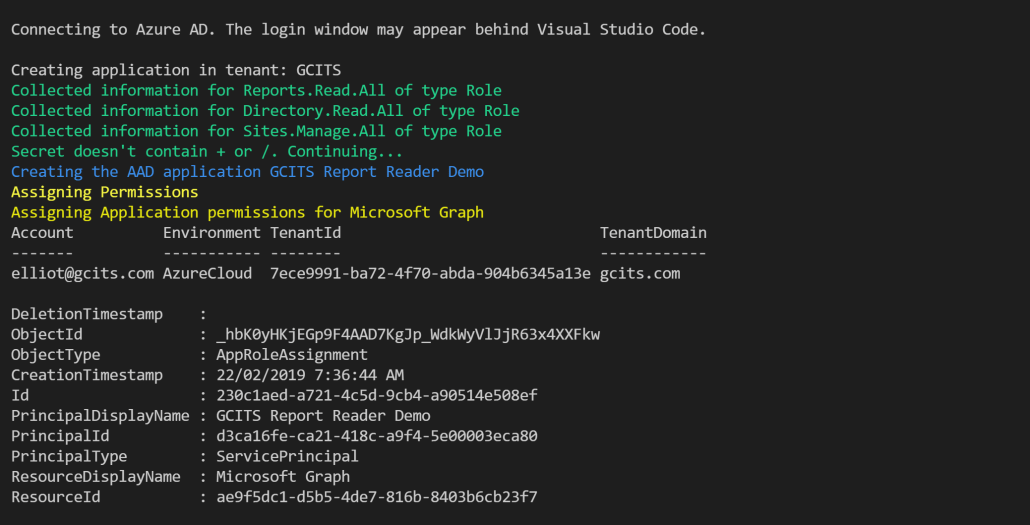
+6. Sign in to Azure AD using your global admin credentials. Note that the login window may appear behind Visual Studio Code.
+7. Wait for the script to complete.![Creating Azure AD Application Via Power Shell]
+
+ 
+
+8. Retrieve the **client ID, client secret and tenant ID** from the exported CSV at C:\\temp\\azureadapp.csv. (below image is just an example.)
+
+ 
+
+
+### PowerShell Script to create and authorise Azure AD Application
+
+```powershell
+# This script needs to be run by an admin account in your Office 365 tenant
+# This script will create an Azure AD app in your organisation with permission
+# to access resources in yours and your customers' tenants.
+# It will export information about the application to a CSV located at C:\temp\.
+# The CSV will include the Client ID and Secret of the application, so keep it safe.
+
+# Confirm C:\temp exists
+$temp = Test-Path -Path C:\temp
+if ($temp) {
+ #Write-Host "Path exists"
+}
+else {
+ Write-Host "Creating Temp folder"
+ New-Item -Path C:\temp -ItemType directory
+}
+
+$applicationName = "GCITS User Activity Report Reader"
+
+# Change this to true if you would like to overwrite any existing applications with matching names.
+$removeExistingAppWithSameName = $false
+# Modify the homePage, appIdURI and logoutURI values to whatever valid URI you like.
+# They don't need to be actual addresses, so feel free to make something up (as long as it's on a verified domain in your Office 365 environment eg. https://anything.yourdomain.com).
+$homePage = "https://secure.gcits.com"
+$appIdURI = "https://secure.gcits.com/$((New-Guid).ToString())"
+$logoutURI = "https://portal.office.com"
+
+$URIForApplicationPermissionCall = "https://graph.microsoft.com/beta/reports/getMailboxUsageDetail(period='D7')?`$format=application/json"
+$ApplicationPermissions = "Reports.Read.All Directory.Read.All Sites.Manage.All"
+
+Function Add-ResourcePermission($requiredAccess, $exposedPermissions, $requiredAccesses, $permissionType) {
+ foreach ($permission in $requiredAccesses.Trim().Split(" ")) {
+ $reqPermission = $null
+ $reqPermission = $exposedPermissions | Where-Object {$_.Value -contains $permission}
+ Write-Host "Collected information for $($reqPermission.Value) of type $permissionType" -ForegroundColor Green
+ $resourceAccess = New-Object Microsoft.Open.AzureAD.Model.ResourceAccess
+ $resourceAccess.Type = $permissionType
+ $resourceAccess.Id = $reqPermission.Id
+ $requiredAccess.ResourceAccess.Add($resourceAccess)
+ }
+}
+
+Function Get-RequiredPermissions($requiredDelegatedPermissions, $requiredApplicationPermissions, $reqsp) {
+ $sp = $reqsp
+ $appid = $sp.AppId
+ $requiredAccess = New-Object Microsoft.Open.AzureAD.Model.RequiredResourceAccess
+ $requiredAccess.ResourceAppId = $appid
+ $requiredAccess.ResourceAccess = New-Object System.Collections.Generic.List[Microsoft.Open.AzureAD.Model.ResourceAccess]
+ if ($requiredDelegatedPermissions) {
+ Add-ResourcePermission $requiredAccess -exposedPermissions $sp.Oauth2Permissions -requiredAccesses $requiredDelegatedPermissions -permissionType "Scope"
+ }
+ if ($requiredApplicationPermissions) {
+ Add-ResourcePermission $requiredAccess -exposedPermissions $sp.AppRoles -requiredAccesses $requiredApplicationPermissions -permissionType "Role"
+ }
+ return $requiredAccess
+}
+Function New-AppKey ($fromDate, $durationInYears, $pw) {
+ $endDate = $fromDate.AddYears($durationInYears)
+ $keyId = (New-Guid).ToString()
+ $key = New-Object Microsoft.Open.AzureAD.Model.PasswordCredential($null, $endDate, $keyId, $fromDate, $pw)
+ return $key
+}
+
+Function Test-AppKey($fromDate, $durationInYears, $pw) {
+
+ $testKey = New-AppKey -fromDate $fromDate -durationInYears $durationInYears -pw $pw
+ while ($testKey.Value -match "\+" -or $testKey.Value -match "/") {
+ Write-Host "Secret contains + or / and may not authenticate correctly. Regenerating..." -ForegroundColor Yellow
+ $pw = Initialize-AppKey
+ $testKey = New-AppKey -fromDate $fromDate -durationInYears $durationInYears -pw $pw
+ }
+ Write-Host "Secret doesn't contain + or /. Continuing..." -ForegroundColor Green
+ $key = $testKey
+
+ return $key
+}
+
+Function Initialize-AppKey {
+ $aesManaged = New-Object "System.Security.Cryptography.AesManaged"
+ $aesManaged.Mode = [System.Security.Cryptography.CipherMode]::CBC
+ $aesManaged.Padding = [System.Security.Cryptography.PaddingMode]::Zeros
+ $aesManaged.BlockSize = 128
+ $aesManaged.KeySize = 256
+ $aesManaged.GenerateKey()
+ return [System.Convert]::ToBase64String($aesManaged.Key)
+}
+function Confirm-MicrosoftGraphServicePrincipal {
+ $graphsp = Get-AzureADServicePrincipal -SearchString "Microsoft Graph"
+ if (!$graphsp) {
+ $graphsp = Get-AzureADServicePrincipal -SearchString "Microsoft.Azure.AgregatorService"
+ }
+ if (!$graphsp) {
+ Login-AzureRmAccount -Credential $credentials
+ New-AzureRmADServicePrincipal -ApplicationId "00000003-0000-0000-c000-000000000000"
+ $graphsp = Get-AzureADServicePrincipal -SearchString "Microsoft Graph"
+ }
+ return $graphsp
+}
+Write-Host "Connecting to Azure AD. The login window may appear behind Visual Studio Code."
+Connect-AzureAD
+
+Write-Host "Creating application in tenant: $((Get-AzureADTenantDetail).displayName)"
+
+# Check for the Microsoft Graph Service Principal. If it doesn't exist already, create it.
+$graphsp = Confirm-MicrosoftGraphServicePrincipal
+
+$existingapp = $null
+$existingapp = get-azureadapplication -SearchString $applicationName
+if ($existingapp -and $removeExistingAppWithSameName) {
+ Remove-Azureadapplication -ObjectId $existingApp.objectId
+}
+
+# RSPS
+$rsps = @()
+if ($graphsp) {
+ $rsps += $graphsp
+ $tenant_id = (Get-AzureADTenantDetail).ObjectId
+ $tenantName = (Get-AzureADTenantDetail).DisplayName
+
+ # Add Required Resources Access (Microsoft Graph)
+ $requiredResourcesAccess = New-Object System.Collections.Generic.List[Microsoft.Open.AzureAD.Model.RequiredResourceAccess]
+ $microsoftGraphRequiredPermissions = Get-RequiredPermissions -reqsp $graphsp -requiredApplicationPermissions $ApplicationPermissions -requiredDelegatedPermissions $DelegatedPermissions
+ $requiredResourcesAccess.Add($microsoftGraphRequiredPermissions)
+
+ # Get an application key
+ $pw = Initialize-AppKey
+ $fromDate = [System.DateTime]::Now
+ $appKey = Test-AppKey -fromDate $fromDate -durationInYears 99 -pw $pw
+
+ Write-Host "Creating the AAD application $applicationName" -ForegroundColor Blue
+ $aadApplication = New-AzureADApplication -DisplayName $applicationName `
+ -HomePage $homePage `
+ -ReplyUrls $homePage `
+ -IdentifierUris $appIdURI `
+ -LogoutUrl $logoutURI `
+ -RequiredResourceAccess $requiredResourcesAccess `
+ -PasswordCredentials $appKey `
+ -AvailableToOtherTenants $true
+
+ # Creating the Service Principal for the application
+ $servicePrincipal = New-AzureADServicePrincipal -AppId $aadApplication.AppId
+
+ Write-Host "Assigning Permissions" -ForegroundColor Yellow
+
+ # Assign application permissions to the application
+ foreach ($app in $requiredResourcesAccess) {
+ $reqAppSP = $rsps | Where-Object {$_.appid -contains $app.ResourceAppId}
+ Write-Host "Assigning Application permissions for $($reqAppSP.displayName)" -ForegroundColor DarkYellow
+ foreach ($resource in $app.ResourceAccess) {
+ if ($resource.Type -match "Role") {
+ New-AzureADServiceAppRoleAssignment -ObjectId $serviceprincipal.ObjectId `
+ -PrincipalId $serviceprincipal.ObjectId -ResourceId $reqAppSP.ObjectId -Id $resource.Id
+ }
+ }
+ }
+
+ # This provides the application with access to your customer tenants.
+ $group = Get-AzureADGroup -Filter "displayName eq 'Adminagents'"
+ Add-AzureADGroupMember -ObjectId $group.ObjectId -RefObjectId $servicePrincipal.ObjectId
+
+ Write-Host "App Created" -ForegroundColor Green
+
+ # Define parameters for Microsoft Graph access token retrieval
+ $client_id = $aadApplication.AppId;
+ $client_secret = $appkey.Value
+ $tenant_id = (Get-AzureADTenantDetail).ObjectId
+ $resource = "https://graph.microsoft.com"
+ $authority = "https://login.microsoftonline.com/$tenant_id"
+ $tokenEndpointUri = "$authority/oauth2/token"
+
+ # Get the access token using grant type password for Delegated Permissions or grant type client_credentials for Application Permissions
+
+ $content = "grant_type=client_credentials&client_id=$client_id&client_secret=$client_secret&resource=$resource"
+
+ # Try to execute the API call 6 times
+
+ $Stoploop = $false
+ [int]$Retrycount = "0"
+ do {
+ try {
+ $response = Invoke-RestMethod -Uri $tokenEndpointUri -Body $content -Method Post -UseBasicParsing
+ Write-Host "Retrieved Access Token" -ForegroundColor Green
+ # Assign access token
+ $access_token = $response.access_token
+ $body = $null
+
+ $body = Invoke-RestMethod `
+ -Uri $UriForApplicationPermissionCall `
+ -Headers @{"Authorization" = "Bearer $access_token"} `
+ -ContentType "application/json" `
+ -Method GET `
+
+ Write-Host "Retrieved Graph content" -ForegroundColor Green
+ $Stoploop = $true
+ }
+ catch {
+ if ($Retrycount -gt 5) {
+ Write-Host "Could not get Graph content after 6 retries." -ForegroundColor Red
+ $Stoploop = $true
+ }
+ else {
+ Write-Host "Could not get Graph content. Retrying in 5 seconds..." -ForegroundColor DarkYellow
+ Start-Sleep -Seconds 5
+ $Retrycount ++
+ }
+ }
+ }
+ While ($Stoploop -eq $false)
+
+ $appInfo = [pscustomobject][ordered]@{
+ ApplicationName = $ApplicationName
+ TenantName = $tenantName
+ TenantId = $tenant_id
+ clientId = $client_id
+ clientSecret = $client_secret
+ ApplicationPermissions = $ApplicationPermissions
+ }
+
+ $AppInfo | Export-Csv C:\temp\AzureADApp.csv -Append -NoTypeInformation
+}
+else {
+ Write-Host "Microsoft Graph Service Principal could not be found or created" -ForegroundColor Red
+}
+
+```
+
+Script 2 – Syncing Office 365 User Reports with IT Glue
+-------------------------------------------------------
+
+This script will run through your Office 365 customers and retrieve Office 365 usage reports. It will also create a SharePoint list containing a register of matches of Office 365 tenants to IT Glue organisations. This script uses the same match register as our [Secure Score to IT Glue guide](https://gcits.com/knowledge-base/sync-microsoft-secure-scores-with-it-glue/), so if you’re using that already, you won’t need to re-match anything.
+
+1. Double click the below script to select it.
+2. Copy and paste the script into a new file in Visual Studio Code and save it with a .ps1 extension
+3. Replace $appId, $secret, and $ourTenantId with your client ID, client secret and Tenant Id values respectively.
+4. Create and retrieve an IT Glue API key by logging in as an IT Glue administrator and navigating to **Account, API Keys** and choosing **Generate API Key**. Paste this key into the $ITGApiKey value
+5. Press F5 to run the script and wait for it to complete.
+6. If you haven’t run our Secure Score to IT Glue script already, the script will stop once it has created a SharePoint list with a register of Office 365 tenant to IT Glue Org matches. To access this list, log onto your root SharePoint site at https://yourtenantname.sharepoint.com
+7. Click the settings cog on the top right, and select **Site Contents**
+8. Locate the **Office 365 – IT Glue match register** list. Edit any incorrect matches by setting DisableSync to Yes
+9. Once you’re happy with your Office 365 Tenant to IT Glue company matches, return to Visual Studio Code and press Enter to continue
+10. Wait for the script to complete, then log into IT Glue and navigate to **Account**, **Customise Sidebar**
+11. Drag the **Office 365 User Report** flexible asset to the sidebar and click **Save.**
+
+### PowerShell script to sync Office 365 User Activity and Usage with IT Glue
+
+```powershell
+# Azure AD App Details
+$client_id = "EnterYourClientIDHere"
+$client_secret = "EnterYourClientSecretHere"
+$ourTenantId = "EnterYourTenantIdHere"
+$ourCompanyName = "EnterYourCompanyNameHere" # eg. GCITS
+$ourDomainName = "EnterYourDefaultDomainHere" # eg. gcits.com
+$ListName = "Office 365 - IT Glue match register"
+$graphBaseUri = "https://graph.microsoft.com/v1.0/"
+$siteid = "root"
+$UserList = "AAD Users"
+
+
+# IT Glue Details
+# EU tenants may need to update this to "https://api.eu.itglue.com"
+$ITGbaseURI = "https://api.itglue.com"
+$ITGkey = "EnterYourITGlueAPIKeyHere"
+$ITGheaders = @{"x-api-key" = $ITGkey }
+$FlexibleAssetName = "Office 365 User Report"
+
+function Get-GCITSAccessToken($appCredential, $tenantId) {
+ $client_id = $appCredential.appID
+ $client_secret = $appCredential.secret
+ $tenant_id = $tenantid
+ $resource = "https://graph.microsoft.com"
+ $authority = "https://login.microsoftonline.com/$tenant_id"
+ $tokenEndpointUri = "$authority/oauth2/token"
+ $content = "grant_type=client_credentials&client_id=$client_id&client_secret=$client_secret&resource=$resource"
+ $response = Invoke-RestMethod -Uri $tokenEndpointUri -Body $content -Method Post -UseBasicParsing
+ $access_token = $response.access_token
+ return $access_token
+}
+
+function Get-GCITSMSGraphResource($Resource) {
+ $graphBaseUri = "https://graph.microsoft.com/beta"
+ $values = @()
+ $result = Invoke-RestMethod -Uri "$graphBaseUri/$resource" -Headers $headers
+ if ($result.value) {
+ $values += $result.value
+ if ($result."@odata.nextLink") {
+ do {
+ $result = Invoke-RestMethod -Uri $result."@odata.nextLink" -Headers $headers
+ $values += $result.value
+ } while ($result."@odata.nextLink")
+ }
+ }
+ else {
+ $values = $result
+ }
+ return $values
+}
+function New-GCITSSharePointColumn($Name, $Type, $Indexed, $lookupListName, $lookupColumnPrimaryName, $lookupColumnName, $longText) {
+ if ($longText) {
+ $column = [ordered]@{
+ name = $Name
+ indexed = $Indexed
+ $Type = @{
+ maxLength = 0
+ allowMultipleLines = $True
+ #appendChangesToExistingText = $False
+ #linesForEditing = 6
+ #textType = "plain"
+ }
+
+ }
+ }
+ else {
+ $column = [ordered]@{
+ name = $Name
+ indexed = $Indexed
+ $Type = @{ }
+ }
+
+ if ($lookupListName -and $type -contains "lookup") {
+ $list = Get-GCITSSharePointList -ListName $lookupListName
+ if ($list) {
+ $column.lookup.listId = $list.id
+ $column.lookup.columnName = $lookupColumnName
+ }
+ }
+ }
+
+ return $column
+}
+function New-GCITSSharePointList ($Name, $ColumnCollection) {
+ $list = @{
+ displayName = $Name
+ columns = $columnCollection
+ } | Convertto-json -Depth 10
+
+ $newList = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method POST -Body $list
+ return $newList
+}
+
+function Remove-GCITSSharePointList ($ListId) {
+ $removeList = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$ListId" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method DELETE
+ return $removeList
+}
+
+function Remove-GCITSSharePointListItem ($ListId, $ItemId) {
+ $removeItem = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$ListId/items/$ItemId" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method DELETE
+ return $removeItem
+}
+
+function New-GCITSSharePointListItem($ItemObject, $ListId) {
+
+ $itemBody = @{
+ fields = $ItemObject
+ } | ConvertTo-Json -Depth 10
+
+ $listItem = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$listId/items" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method Post `
+ -Body $itemBody
+}
+
+function Get-GCITSSharePointListItem($ListId, $ItemId, $Query) {
+
+ if ($ItemId) {
+ $listItem = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items/$ItemId `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = $listItem
+ }
+ elseif ($Query) {
+ $listItems = $null
+ $listItems = Invoke-RestMethod -Uri "$graphBaseUri/sites/$siteid/lists/$listId/items/?expand=fields&`$filter=$Query" `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = @()
+ $value = $listItems.value
+ if ($listitems."@odata.nextLink") {
+ $nextLink = $true
+ }
+ if ($nextLink) {
+ do {
+ $listItems = Invoke-RestMethod -Uri $listitems."@odata.nextLink"`
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value += $listItems.value
+ if (!$listitems."@odata.nextLink") {
+ $nextLink = $false
+ }
+ } until (!$nextLink)
+ }
+ }
+ else {
+ $listItems = $null
+ $listItems = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items?expand=fields `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = @()
+ $value = $listItems.value
+ if ($listitems."@odata.nextLink") {
+ $nextLink = $true
+ }
+ if ($nextLink) {
+ do {
+ $listItems = Invoke-RestMethod -Uri $listitems."@odata.nextLink"`
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value += $listItems.value
+ if (!$listitems."@odata.nextLink") {
+ $nextLink = $false
+ }
+ } until (!$nextLink)
+ }
+ }
+ return $value
+}
+
+function Set-GCITSSharePointListItem($ListId, $ItemId, $ItemObject) {
+ $listItem = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items/$ItemId/fields `
+ -Method Patch -headers $SPHeaders `
+ -ContentType application/json `
+ -Body ($itemObject | ConvertTo-Json)
+ $return = $listItem
+}
+
+function Get-GCITSSharePointList($ListName) {
+ $list = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists?expand=columns&`$filter=displayName eq '$ListName'" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method GET
+ $list = $list.value
+ return $list
+}
+Function Get-GCITSMSGraphReport ($ReportName, $Resource) {
+ $Report = Get-GCITSMSGraphResource -Resource $Resource
+ if ($Report) {
+ $Report | Add-Member ReportName $ReportName -Force
+ }
+ Write-Host "$reportname - $($report.count)"
+ return $Report
+}
+
+function Get-GCITSSpacingTitleCase ($String) {
+ $String = ($String -creplace '([A-Z\W_]|\d+)(?$(Get-GCITSSpacingTitleCase -String $objectproperty): $($object.$($objectProperty))"
+ }
+ }
+ $reportKeyValue = $stringArray -join "
"
+ }
+ elseif ($reportKey.OriginalPropertyName -eq "assignedLicenses") {
+ $stringArray = @()
+ foreach ($license in $reportKeyValue) {
+ $stringArray += ($licenses | Where-Object { $_.skuid -eq $license.skuid }).skupartnumber
+ }
+ $reportKeyValue = $stringArray -join ", "
+ }
+ elseif ($reportKey.OriginalPropertyName -eq "proxyAddresses") {
+ $stringArray = @()
+ foreach ($address in $reportKeyValue) {
+ $stringArray += ($address -split ":")[1]
+ }
+ $reportKeyValue = $stringArray -join ", "
+
+ }
+ else {
+ if (($reportKeyValue[0].psobject.properties.name | Measure-Object).count -gt 0) {
+ $reportKeyValue = "Detected"
+ }
+ else {
+ $reportKeyValue = "None"
+ }
+ }
+
+ }
+ if ($reportKeyValue -and $field) {
+ $userReportTraits | Add-member $field.'name-key' $reportKeyValue -Force
+ }
+ }
+ }
+
+ foreach ($ITGOrg in $ITGOrgToSync) {
+ $FlexibleAssetBody = [pscustomobject]@{
+ data = @{
+ type = "flexible-assets"
+ attributes = [pscustomobject]@{
+ "organization-id" = $ITGOrg.fields.ITGlueOrgId
+ "flexible-asset-type-id" = $flexibleAsset.id
+ traits = $userReportTraits
+ }
+ }
+ }
+
+ $FlexibleAssetItem = $FlexibleAssetBody | ConvertTo-Json -Depth 10
+ try {
+ $existingFlexibleAssetsForUser = $existingFlexibleAssetsForTenant | Where-Object { $_.attributes.traits.id -eq $user.id -and $_.attributes.'organization-id' -eq $ITGOrg.fields.ITGlueOrgId } | Select-Object -First 1
+ if ($existingFlexibleAssetsForUser) {
+ $updateItem = Set-GCITSITGItem -Resource flexible_assets -existingItem $existingFlexibleAssetsForUser -Body $FlexibleAssetItem
+ }
+ else {
+ $newItem = New-GCITSITGItem -resource flexible_assets -body $FlexibleAssetItem
+ }
+ }
+ catch {
+ Write-Host "Error here: $($error[0])"
+ }
+ }
+ }
+ $TenantsToDisable = $ITGOrgsForTenant | where-object { $_.fields.DisableSync }
+ # Remove Office 365 user reports from tenants where sync is disabled in SharePoint List
+ foreach ($tenant in $TenantsToDisable) {
+ $assetsToRemove = $existingFlexibleAssetsForTenant | Where-Object { $_.attributes.'organization-id' -eq $tenant.fields.ITGlueOrgId }
+ if ($assetsToRemove) {
+ foreach ($item in $assetsToRemove) {
+ Write-Host "Removing $($item.attributes.traits.'user-principal-name') from $($tenant.fields.ITGlueOrg)"
+ Remove-GCITSITGItem -Resource flexible_assets -ExistingItem $item
+ }
+ }
+ }
+ }
+ }
+}
+
+<#
+# If you want to clear out all existing assets, just uncomment and run the following script block once you've initialised the variables and functions at the top of the script.
+# You can do this by selecting the code and pressing F8.
+
+$flexibleAsset = Get-GCITSITGItem -Resource "flexible_asset_types?filter[name]=$FlexibleAssetName"
+[array]$existingAssets = Get-GCITSITGItem -Resource "flexible_assets?filter[organization_id]=$($ITGCompany)&filter[flexible_asset_type_id]=$($flexibleasset.id)"
+
+foreach($item in $existingAssets){
+ Write-Host "Removing $($item.attributes.traits.'user-principal-name')"
+ Remove-GCITSITGItem -Resource flexible_assets -ExistingItem $item
+```
\ No newline at end of file
diff --git a/OrganisationSharePointSync/README.md b/OrganisationSharePointSync/README.md
new file mode 100644
index 0000000..d19d536
--- /dev/null
+++ b/OrganisationSharePointSync/README.md
@@ -0,0 +1,323 @@
+[Source](https://gcits.com/knowledge-base/sync-it-glue-organisations-with-a-sharepoint-list-via-powershell/ "Permalink to Sync IT Glue organisations with a SharePoint List via PowerShell")
+
+# Sync IT Glue organisations with a SharePoint List via PowerShell
+
+This script will create a SharePoint list on your root SharePoint site called '**ITGlue Org Register**' populated with some basic details for each of your IT Glue organisations.
+
+We refer to this SharePoint List in some of our other guides. It's used as a reference for matching configurations and flexible assets with the correct IT Glue organisation.
+
+This script is intended to be run on a schedule within a timer triggered PowerShell Azure Function, however you can also run it as a scheduled task.
+
+### Prerequisites
+
+- You'll need to first create a SharePoint Application in your Azure AD tenant with the Sites.Manage.All permission. If you haven't done this already, [use this script][1] to create the application and retrieve the **Tenant ID**, **Client ID** and **Client Secret** from the exported CSV.![Retrieve Application Tenant ID Client ID And Secret From CSV][2]
+- You'll also need to retrieve or generate an API key for IT Glue under **Account**, **Settings**, **API Keys. ![Get IT Glue API Key][3]**
+
+## How to sync your IT Glue organisations with a SharePoint List via PowerShell
+
+1. It's a good idea to run the script locally first to confirm that it works. Double click the script below to select it, then copy and paste it into a new file in Visual Studio Code
+2. Save the file with a **.ps1** extension and, if you haven't already, install the recommended PowerShell extension.
+3. Replace the **$key** variable with your IT Glue API key, then replace the **$tenant_id**, **$client_id** and **$client_secret** variables with the relevant values from the CSV at C:tempAzureADApp. If you haven't created this app yet, [follow this quick guide here][1]. ![Update Variables In Visual Studio Code][4]
+4. Press **F5** to run the script.
+5. On its first run, it will create the SharePoint list, then populate it with the basic information from your IT Glue organisations. On subsequent runs, it will update the item, or delete organisations from the list which no longer exist in IT Glue. Once you have tested the script in Visual Studio Code, continue following along below to set it up in an Azure Function.![Creating SharePoint List On First Run][5]
+
+## PowerShell script to sync IT Glue Organisations with a SharePoint List
+
+```powershell
+ <#
+ This script will sync IT Glue organisations with a SharePoint list in the root sharepoint site (eg tenantname.sharepoint.com).
+ The list is called 'ITGlue Org Register'
+ It should be run on a schedule to keep the SharePoint list up to date.
+ #>
+
+ [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
+ $key = "EnterYourITGlueAPIKeyHere"
+ # Note that EU hosted IT Glue Tenants may need to update the below value to "https://api.eu.itglue.com"
+ $ITGbaseURI = "https://api.itglue.com"
+ $headers = @{
+ "x-api-key" = $key
+ }
+ $client_id = "EnterYourSharePointAppClientIDHere"
+ $client_secret = "EnterYourSharePointAppClientSecretHere"
+ $tenant_id = "EnterYourTenantIDHere"
+ $graphBaseUri = "https://graph.microsoft.com/v1.0/"
+ $siteid = "root"
+ $ListName = "ITGlue Org Register"
+
+ function Get-GCITSITGlueItem($Resource) {
+ $array = @()
+ $body = Invoke-RestMethod -Method get -Uri "$ITGbaseUri/$Resource" -Headers $headers -ContentType application/vnd.api+json
+ $array += $body.data
+ if ($body.links.next) {
+ do {
+ $body = Invoke-RestMethod -Method get -Uri $body.links.next -Headers $headers -ContentType application/vnd.api+json
+ $array += $body.data
+ } while ($body.links.next)
+ }
+ return $array
+ }
+
+ function New-GCITSSharePointColumn($Name, $Type, $Indexed) {
+ $column = [ordered]@{
+ name = $Name
+ indexed = $Indexed
+ $Type = @{}
+ }
+ return $column
+ }
+
+ function New-GCITSSharePointList ($Name, $ColumnCollection) {
+ $list = @{
+ displayName = $Name
+ columns = $columnCollection
+ } | Convertto-json -Depth 10
+
+ $newList = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method POST -Body $list
+ return $newList
+ }
+
+ function Remove-GCITSSharePointList ($ListId) {
+ $removeList = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$ListId" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method DELETE
+ return $removeList
+ }
+
+ function Remove-GCITSSharePointListItem ($ListId, $ItemId) {
+ $removeItem = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$ListId/items/$ItemId" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method DELETE
+ return $removeItem
+ }
+
+ function New-GCITSSharePointListItem($ItemObject, $ListId) {
+
+ $itemBody = @{
+ fields = $ItemObject
+ } | ConvertTo-Json -Depth 10
+
+ $listItem = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$listId/items" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method Post `
+ -Body $itemBody
+ }
+
+ function Get-GCITSSharePointItem($ListId, $ItemId) {
+
+ if ($ItemId) {
+ $listItem = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items/$ItemId `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = $listItem
+ }
+ else {
+ $listItems = $null
+ $listItems = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items?expand=fields `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = @()
+ $value = $listItems.value
+ if ($listitems."@odata.nextLink") {
+ $nextLink = $true
+ }
+ if ($nextLink) {
+ do {
+ $listItems = Invoke-RestMethod -Uri $listitems."@odata.nextLink"`
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value += $listItems.value
+ if (!$listitems."@odata.nextLink") {
+ $nextLink = $false
+ }
+ } until (!$nextLink)
+ }
+ }
+ return $value
+ }
+
+ function Set-GCITSSharePointListItem($ListId, $ItemId, $ItemObject) {
+ $listItem = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items/$ItemId/fields `
+ -Method Patch -headers $SPHeaders `
+ -ContentType application/json `
+ -Body ($itemObject | ConvertTo-Json)
+ $return = $listItem
+ }
+
+ function Get-GCITSAccessToken {
+ $authority = "https://login.microsoftonline.com/$tenant_id"
+ $tokenEndpointUri = "$authority/oauth2/token"
+ $resource = "https://graph.microsoft.com"
+ $content = "grant_type=client_credentials&client_id=$client_id&client_secret=$client_secret&resource=$resource"
+ $graphBaseUri = "https://graph.microsoft.com/v1.0"
+ $response = Invoke-RestMethod -Uri $tokenEndpointUri -Body $content -Method Post -UseBasicParsing
+ $access_token = $response.access_token
+ return $access_token
+ }
+
+ function Get-GCITSMSGraphResource($Resource) {
+ $graphBaseUri = "https://graph.microsoft.com/v1.0"
+ $values = @()
+ $result = Invoke-RestMethod -Uri "$graphBaseUri/$resource" -Headers $headers
+ $values += $result.value
+ if ($result.'@odata.nextLink') {
+ do {
+ $result = Invoke-RestMethod -Uri $result.'@odata.nextLink' -Headers $headers
+ $values += $result.value
+ } while ($result.'@odata.nextLink')
+ }
+ return $values
+ }
+
+ function Get-GCITSSharePointList($ListName) {
+ $list = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists?expand=columns&`$filter=displayName eq '$ListName'" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method GET
+ $list = $list.value
+ return $list
+ }
+
+ $organisations = Get-GCITSITGlueItem -Resource organizations
+
+ $access_token = Get-GCITSAccessToken
+ $SPHeaders = @{Authorization = "Bearer $access_token"}
+
+ $list = Get-GCITSSharePointList -ListName $ListName
+
+ if (!$list) {
+ Write-Output "List not found, creating List"
+ # Initiate Columns
+ $columnCollection = @()
+ $columnCollection += New-GCITSSharePointColumn -Name ShortName -Type text -Indexed $true
+ $columnCollection += New-GCITSSharePointColumn -Name ITGlueID -Type number -Indexed $true
+
+ $List = New-GCITSSharePointList -Name $ListName -ColumnCollection $columnCollection
+ }
+ else {
+ Write-Output "List Exists, retrieving existing items"
+ $existingItems = Get-GCITSSharePointItem -ListId $list.id
+ Write-Output "Retrieved $($existingItems.count) existing items"
+ }
+
+ foreach ($organisation in $organisations) {
+ Write-Output "Checking $($organisation.attributes.Name)"
+ $existingitem = $existingItems | Where-Object {$_.fields.ITGlueID -contains $organisation.id}
+
+ # if there is no match in SharePoint for the existing org, create the item
+ if (!$existingitem) {
+ $item = @{
+ "Title" = $organisation.attributes.name
+ "ShortName" = $organisation.attributes.'short-name'
+ "ITGlueID" = $organisation.id
+ }
+ Write-Output "Creating $($organisation.attributes.Name)"
+ New-GCITSSharePointListItem -ListId $list.id -ItemObject $item
+ }
+ else {
+ if ($existingitem.fields.Title -notcontains $organisation.attributes.name `
+ -or $existingitem.fields.ShortName -notcontains $organisation.attributes.'short-name') {
+ Write-Output "Updating $($organisation.attributes.Name)"
+ $item = @{
+ "Title" = $organisation.attributes.name
+ "ShortName" = $organisation.attributes.'short-name'
+ "ITGlueID" = $organisation.id
+ }
+ Set-GCITSSharePointListItem -ListId $list.Id -ItemId $existingitem.id -ItemObject $item
+ }
+ }
+ }
+ Write-Output "Cleaning up"
+
+ foreach ($existingItem in $existingItems) {
+
+ if ($organisations.id -notcontains $existingitem.fields.itglueid) {
+ Write-Output "Couldn't resolve, removing $($existingItem.fields.title)"
+ $removeItem = Remove-GCITSSharePointListItem -ListId $listId -ItemId $existingitem.id
+ }
+
+ }
+```
+
+## How to run this script as an Azure Function
+
+You might have noticed that this script uses Write-Output instead of Write-Host for it's outputs. This is because it's intended to be run in an Azure Function. Write-Host doesn't display any output in Azure Functions, while Write-Output does. If you'd prefer not to set this up as an Azure Function, you can also run it as a scheduled task.
+
+### Setting up the Azure Function App
+
+1. Login to as a user with the ability to create resources in a subscription
+2. [Create an Azure Function app by following this guide][6]. Or choose one you've already created.
+
+Note: If you are creating a new Azure Function App, you will be given the choice between a function app on an App Service Plan, or a Consumption Plan.
+
+Consumption plans are generally much cheaper, however the scripts that you run on them will automatically time out after around 5 minutes. For many organisations, this script will finish within the 5 minute time period. If you anticipate that you'll be running other long running scripts on this Azure Function App, you may decide to create one with a dedicated App Service Plan. Pricing for the underlying app service is shown to you when setting up the function app.
+
+3. Once you have created your Azure Function App, you can create an Azure Function for the script. Click the **+** icon
+ ![Create New Azure Function][7]
+4. Click the toggle for **Enable experimental language support**
+ ![Enable Experimental Language Support][8]
+5. Choose **PowerShell** under **Timer Triggered Functions**
+ ![Create Timer Trigger PowerShell Azure Function][9]
+6. Give it a name like\***\* TT-SyncITGOrgSP \*\***and define a cron schedule for it to run on. In this example we want it to run every 12 hours:
+
+```cron
+ 0 0 */12 * * *
+```
+
+![New Timer Trigger Function Name And Schedule][10]
+
+7. Copy and paste the script from Visual Studio Code into your new Azure Function.
+8. Press the **Save and Run** button.
+9. You will see the progress of the script in the logs at the bottom of the page.![IT Glue SharePoint Sync Running In Azure Functions][11]
+
+### Secure your keys in the Azure Function
+
+Once you have confirmed that the script runs without issue, you can hide your IT Glue API Key and SharePoint Client Secret in the Applications Settings of the function.
+
+1. Click the name of your Azure Function app on the left menu. In this example our Function App is called **gcitsops**. Then click **Application Settings**.![Open Application Settings For Azure Function][12]
+2. Scroll down to Application Settings and add two new settings called **ITGAPIKey** and **SharePointClientSecret**. Paste the IT Glue API Key and the SharePoint app's client secret into these new values. Scroll to the top of the page and click **Save**.![Store API Keys In Azure Function Application Settings][13]
+3. Return to your function and replace the values for $key and $client_secret with** $env:ITGAPIKey** and **$env:SharePointClientSecret![Update Variables In Azure Function With Application Setting Environment Variables][14]**
+4. Save and Run your function to confirm it's working.
+
+## View your new List on SharePoint
+
+The list that is created by this script can be found on your root SharePoint site (eg. tenantname.sharepoint.com). If it is not appearing under recent items on the left menu, you'll find it under **Site Contents**, **ITGlue Org Register**.
+
+![SharePoint List Of IT Glue Organisations][15]
+
+### About The Author
+
+![Elliot Munro][16]
+
+#### [ Elliot Munro ][17]
+
+Elliot Munro is an Office 365 MCSA from the Gold Coast, Australia supporting hundreds of small businesses with GCITS. If you have an Office 365 or Azure issue that you'd like us to take a look at (or have a request for a useful script) send Elliot an email at [elliot@gcits.com][18]
+
+[1]: https://gcits.com/knowledge-base/create-a-sharepoint-application-for-the-microsoft-graph-via-powershell/
+[2]: https://gcits.com/wp-content/uploads/RetrieveApplicationTenantIDClientIDAndSecretFromCSV-1030x261.png
+[3]: https://gcits.com/wp-content/uploads/GetITGlueAPIKey-1030x453.png
+[4]: https://gcits.com/wp-content/uploads/UpdateVariablesInVisualStudioCode-1030x384.png
+[5]: https://gcits.com/wp-content/uploads/CreatingSharePointListOnFirstRun.png
+[6]: https://docs.microsoft.com/en-us/azure/azure-functions/functions-create-function-app-portal
+[7]: https://gcits.com/wp-content/uploads/CreateNewAzureFunction.png
+[8]: https://gcits.com/wp-content/uploads/EnableExperimentalLanguageSupport.png
+[9]: https://gcits.com/wp-content/uploads/CreateTimerTriggerPowerShellAzureFunction.png
+[10]: https://gcits.com/wp-content/uploads/NewTimerTriggerFunctionNameAndSchedule-1030x598.png
+[11]: https://gcits.com/wp-content/uploads/ITGlueSharePointSyncRunningInAzureFunctions-1030x239.png
+[12]: https://gcits.com/wp-content/uploads/OpenApplicationSettingsForAzureFunction-1030x687.png
+[13]: https://gcits.com/wp-content/uploads/StoreAPIKeysInAzureFunctionApplicationSettings-1030x362.png
+[14]: https://gcits.com/wp-content/uploads/UpdateVariablesInAzureFunctionWithApplicationSettingEnvironmentVariables-1030x243.png
+[15]: https://gcits.com/wp-content/uploads/SharePointListOfITGlueOrganisations-1030x426.png
+[16]: https://gcits.com/wp-content/uploads/AAEAAQAAAAAAAA2QAAAAJDNlN2NmM2Y4LTU5YWYtNGRiNC1hMmI2LTBhMzdhZDVmNWUzNA-80x80.jpg
+[17]: https://gcits.com/author/elliotmunro/
+[18]: mailto:elliot%40gcits.com
diff --git a/OrganisationSharePointSync/single.ps1 b/OrganisationSharePointSync/single.ps1
new file mode 100644
index 0000000..cdd61cf
--- /dev/null
+++ b/OrganisationSharePointSync/single.ps1
@@ -0,0 +1,223 @@
+<#
+This script will sync IT Glue organisations with a SharePoint list in the root sharepoint site (eg tenantname.sharepoint.com).
+The list is called 'ITGlue Org Register'
+It should be run on a schedule to keep the SharePoint list up to date.
+#>
+
+[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
+$key = "EnterYourITGlueAPIKeyHere"
+# Note that EU hosted IT Glue Tenants may need to update the below value to "https://api.eu.itglue.com"
+$ITGbaseURI = "https://api.itglue.com"
+$headers = @{
+ "x-api-key" = $key
+}
+$client_id = "EnterYourSharePointAppClientIDHere"
+$client_secret = "EnterYourSharePointAppClientSecretHere"
+$tenant_id = "EnterYourTenantIDHere"
+$graphBaseUri = "https://graph.microsoft.com/v1.0/"
+$siteid = "root"
+$ListName = "ITGlue Org Register"
+
+function Get-GCITSITGlueItem($Resource) {
+ $array = @()
+ $body = Invoke-RestMethod -Method get -Uri "$ITGbaseUri/$Resource" -Headers $headers -ContentType application/vnd.api+json
+ $array += $body.data
+ if ($body.links.next) {
+ do {
+ $body = Invoke-RestMethod -Method get -Uri $body.links.next -Headers $headers -ContentType application/vnd.api+json
+ $array += $body.data
+ } while ($body.links.next)
+ }
+ return $array
+}
+
+function New-GCITSSharePointColumn($Name, $Type, $Indexed) {
+ $column = [ordered]@{
+ name = $Name
+ indexed = $Indexed
+ $Type = @{}
+ }
+ return $column
+}
+
+function New-GCITSSharePointList ($Name, $ColumnCollection) {
+ $list = @{
+ displayName = $Name
+ columns = $columnCollection
+ } | Convertto-json -Depth 10
+
+ $newList = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method POST -Body $list
+ return $newList
+}
+
+function Remove-GCITSSharePointList ($ListId) {
+ $removeList = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$ListId" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method DELETE
+ return $removeList
+}
+
+function Remove-GCITSSharePointListItem ($ListId, $ItemId) {
+ $removeItem = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$ListId/items/$ItemId" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method DELETE
+ return $removeItem
+}
+
+function New-GCITSSharePointListItem($ItemObject, $ListId) {
+
+ $itemBody = @{
+ fields = $ItemObject
+ } | ConvertTo-Json -Depth 10
+
+ $listItem = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$listId/items" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method Post `
+ -Body $itemBody
+}
+
+function Get-GCITSSharePointItem($ListId, $ItemId) {
+
+ if ($ItemId) {
+ $listItem = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items/$ItemId `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = $listItem
+ }
+ else {
+ $listItems = $null
+ $listItems = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items?expand=fields `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = @()
+ $value = $listItems.value
+ if ($listitems."@odata.nextLink") {
+ $nextLink = $true
+ }
+ if ($nextLink) {
+ do {
+ $listItems = Invoke-RestMethod -Uri $listitems."@odata.nextLink"`
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value += $listItems.value
+ if (!$listitems."@odata.nextLink") {
+ $nextLink = $false
+ }
+ } until (!$nextLink)
+ }
+ }
+ return $value
+}
+
+function Set-GCITSSharePointListItem($ListId, $ItemId, $ItemObject) {
+ $listItem = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items/$ItemId/fields `
+ -Method Patch -headers $SPHeaders `
+ -ContentType application/json `
+ -Body ($itemObject | ConvertTo-Json)
+ $return = $listItem
+}
+
+function Get-GCITSAccessToken {
+ $authority = "https://login.microsoftonline.com/$tenant_id"
+ $tokenEndpointUri = "$authority/oauth2/token"
+ $resource = "https://graph.microsoft.com"
+ $content = "grant_type=client_credentials&client_id=$client_id&client_secret=$client_secret&resource=$resource"
+ $graphBaseUri = "https://graph.microsoft.com/v1.0"
+ $response = Invoke-RestMethod -Uri $tokenEndpointUri -Body $content -Method Post -UseBasicParsing
+ $access_token = $response.access_token
+ return $access_token
+}
+
+function Get-GCITSMSGraphResource($Resource) {
+ $graphBaseUri = "https://graph.microsoft.com/v1.0"
+ $values = @()
+ $result = Invoke-RestMethod -Uri "$graphBaseUri/$resource" -Headers $headers
+ $values += $result.value
+ if ($result.'@odata.nextLink') {
+ do {
+ $result = Invoke-RestMethod -Uri $result.'@odata.nextLink' -Headers $headers
+ $values += $result.value
+ } while ($result.'@odata.nextLink')
+ }
+ return $values
+}
+
+function Get-GCITSSharePointList($ListName) {
+ $list = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists?expand=columns&`$filter=displayName eq '$ListName'" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method GET
+ $list = $list.value
+ return $list
+}
+
+$organisations = Get-GCITSITGlueItem -Resource organizations
+
+$access_token = Get-GCITSAccessToken
+$SPHeaders = @{Authorization = "Bearer $access_token"}
+
+$list = Get-GCITSSharePointList -ListName $ListName
+
+if (!$list) {
+ Write-Output "List not found, creating List"
+ # Initiate Columns
+ $columnCollection = @()
+ $columnCollection += New-GCITSSharePointColumn -Name ShortName -Type text -Indexed $true
+ $columnCollection += New-GCITSSharePointColumn -Name ITGlueID -Type number -Indexed $true
+
+ $List = New-GCITSSharePointList -Name $ListName -ColumnCollection $columnCollection
+}
+else {
+ Write-Output "List Exists, retrieving existing items"
+ $existingItems = Get-GCITSSharePointItem -ListId $list.id
+ Write-Output "Retrieved $($existingItems.count) existing items"
+}
+
+foreach ($organisation in $organisations) {
+ Write-Output "Checking $($organisation.attributes.Name)"
+ $existingitem = $existingItems | Where-Object {$_.fields.ITGlueID -contains $organisation.id}
+
+ # if there is no match in SharePoint for the existing org, create the item
+ if (!$existingitem) {
+ $item = @{
+ "Title" = $organisation.attributes.name
+ "ShortName" = $organisation.attributes.'short-name'
+ "ITGlueID" = $organisation.id
+ }
+ Write-Output "Creating $($organisation.attributes.Name)"
+ New-GCITSSharePointListItem -ListId $list.id -ItemObject $item
+ }
+ else {
+ if ($existingitem.fields.Title -notcontains $organisation.attributes.name `
+ -or $existingitem.fields.ShortName -notcontains $organisation.attributes.'short-name') {
+ Write-Output "Updating $($organisation.attributes.Name)"
+ $item = @{
+ "Title" = $organisation.attributes.name
+ "ShortName" = $organisation.attributes.'short-name'
+ "ITGlueID" = $organisation.id
+ }
+ Set-GCITSSharePointListItem -ListId $list.Id -ItemId $existingitem.id -ItemObject $item
+ }
+ }
+}
+Write-Output "Cleaning up"
+
+foreach ($existingItem in $existingItems) {
+
+ if ($organisations.id -notcontains $existingitem.fields.itglueid) {
+ Write-Output "Couldn't resolve, removing $($existingItem.fields.title)"
+ $removeItem = Remove-GCITSSharePointListItem -ListId $listId -ItemId $existingitem.id
+ }
+
+}
\ No newline at end of file
diff --git a/SyncMicrosoftSecureScoreReports/CreateApp.ps1 b/SyncMicrosoftSecureScoreReports/CreateApp.ps1
new file mode 100644
index 0000000..a838ffb
--- /dev/null
+++ b/SyncMicrosoftSecureScoreReports/CreateApp.ps1
@@ -0,0 +1,222 @@
+# This script needs to be run by an admin account in your Office 365 tenant
+# This script will create an Azure AD app in your organisation with permission
+# to access resources in yours and your customers' tenants.
+# It will export information about the application to a CSV located at C:\temp\.
+# The CSV will include the Client ID and Secret of the application, so keep it safe.
+
+# Confirm C:\temp exists
+$temp = Test-Path -Path C:\temp
+if ($temp) {
+ #Write-Host "Path exists"
+}
+else {
+ Write-Host "Creating Temp folder"
+ New-Item -Path C:\temp -ItemType directory
+}
+
+$applicationName = "GCITS Secure Score Reader"
+
+# Change this to true if you would like to overwrite any existing applications with matching names.
+$removeExistingAppWithSameName = $false
+# Modify the homePage, appIdURI and logoutURI values to whatever valid URI you like.
+# They don't need to be actual addresses, so feel free to make something up.
+$homePage = "https://secure.gcits.com"
+$appIdURI = "https://secure.gcits.com/$((New-Guid).ToString())"
+$logoutURI = "https://portal.office.com"
+
+$URIForApplicationPermissionCall = "https://graph.microsoft.com/beta/security/secureScores"
+$ApplicationPermissions = "SecurityEvents.Read.All Directory.Read.All Sites.Manage.All"
+
+Function Add-ResourcePermission($requiredAccess, $exposedPermissions, $requiredAccesses, $permissionType) {
+ foreach ($permission in $requiredAccesses.Trim().Split(" ")) {
+ $reqPermission = $null
+ $reqPermission = $exposedPermissions | Where-Object {$_.Value -contains $permission}
+ Write-Host "Collected information for $($reqPermission.Value) of type $permissionType" -ForegroundColor Green
+ $resourceAccess = New-Object Microsoft.Open.AzureAD.Model.ResourceAccess
+ $resourceAccess.Type = $permissionType
+ $resourceAccess.Id = $reqPermission.Id
+ $requiredAccess.ResourceAccess.Add($resourceAccess)
+ }
+}
+
+Function Get-RequiredPermissions($requiredDelegatedPermissions, $requiredApplicationPermissions, $reqsp) {
+ $sp = $reqsp
+ $appid = $sp.AppId
+ $requiredAccess = New-Object Microsoft.Open.AzureAD.Model.RequiredResourceAccess
+ $requiredAccess.ResourceAppId = $appid
+ $requiredAccess.ResourceAccess = New-Object System.Collections.Generic.List[Microsoft.Open.AzureAD.Model.ResourceAccess]
+ if ($requiredDelegatedPermissions) {
+ Add-ResourcePermission $requiredAccess -exposedPermissions $sp.Oauth2Permissions -requiredAccesses $requiredDelegatedPermissions -permissionType "Scope"
+ }
+ if ($requiredApplicationPermissions) {
+ Add-ResourcePermission $requiredAccess -exposedPermissions $sp.AppRoles -requiredAccesses $requiredApplicationPermissions -permissionType "Role"
+ }
+ return $requiredAccess
+}
+Function New-AppKey ($fromDate, $durationInYears, $pw) {
+ $endDate = $fromDate.AddYears($durationInYears)
+ $keyId = (New-Guid).ToString()
+ $key = New-Object Microsoft.Open.AzureAD.Model.PasswordCredential($null, $endDate, $keyId, $fromDate, $pw)
+ return $key
+}
+
+Function Test-AppKey($fromDate, $durationInYears, $pw) {
+
+ $testKey = New-AppKey -fromDate $fromDate -durationInYears $durationInYears -pw $pw
+ while ($testKey.Value -match "\+" -or $testKey.Value -match "/") {
+ Write-Host "Secret contains + or / and may not authenticate correctly. Regenerating..." -ForegroundColor Yellow
+ $pw = Initialize-AppKey
+ $testKey = New-AppKey -fromDate $fromDate -durationInYears $durationInYears -pw $pw
+ }
+ Write-Host "Secret doesn't contain + or /. Continuing..." -ForegroundColor Green
+ $key = $testKey
+
+ return $key
+}
+
+Function Initialize-AppKey {
+ $aesManaged = New-Object "System.Security.Cryptography.AesManaged"
+ $aesManaged.Mode = [System.Security.Cryptography.CipherMode]::CBC
+ $aesManaged.Padding = [System.Security.Cryptography.PaddingMode]::Zeros
+ $aesManaged.BlockSize = 128
+ $aesManaged.KeySize = 256
+ $aesManaged.GenerateKey()
+ return [System.Convert]::ToBase64String($aesManaged.Key)
+}
+function Confirm-MicrosoftGraphServicePrincipal {
+ $graphsp = Get-AzureADServicePrincipal -SearchString "Microsoft Graph"
+ if (!$graphsp) {
+ $graphsp = Get-AzureADServicePrincipal -SearchString "Microsoft.Azure.AgregatorService"
+ }
+ if (!$graphsp) {
+ Login-AzureRmAccount -Credential $credentials
+ New-AzureRmADServicePrincipal -ApplicationId "00000003-0000-0000-c000-000000000000"
+ $graphsp = Get-AzureADServicePrincipal -SearchString "Microsoft Graph"
+ }
+ return $graphsp
+}
+Write-Host "Connecting to Azure AD. The login window may appear behind Visual Studio Code."
+Connect-AzureAD
+
+Write-Host "Creating application in tenant: $((Get-AzureADTenantDetail).displayName)"
+
+# Check for the Microsoft Graph Service Principal. If it doesn't exist already, create it.
+$graphsp = Confirm-MicrosoftGraphServicePrincipal
+
+$existingapp = $null
+$existingapp = get-azureadapplication -SearchString $applicationName
+if ($existingapp -and $removeExistingAppWithSameName) {
+ Remove-Azureadapplication -ObjectId $existingApp.objectId
+}
+
+# RSPS
+$rsps = @()
+if ($graphsp) {
+ $rsps += $graphsp
+ $tenant_id = (Get-AzureADTenantDetail).ObjectId
+ $tenantName = (Get-AzureADTenantDetail).DisplayName
+
+ # Add Required Resources Access (Microsoft Graph)
+ $requiredResourcesAccess = New-Object System.Collections.Generic.List[Microsoft.Open.AzureAD.Model.RequiredResourceAccess]
+ $microsoftGraphRequiredPermissions = Get-RequiredPermissions -reqsp $graphsp -requiredApplicationPermissions $ApplicationPermissions -requiredDelegatedPermissions $DelegatedPermissions
+ $requiredResourcesAccess.Add($microsoftGraphRequiredPermissions)
+
+ # Get an application key
+ $pw = Initialize-AppKey
+ $fromDate = [System.DateTime]::Now
+ $appKey = Test-AppKey -fromDate $fromDate -durationInYears 99 -pw $pw
+
+ Write-Host "Creating the AAD application $applicationName" -ForegroundColor Blue
+ $aadApplication = New-AzureADApplication -DisplayName $applicationName `
+ -HomePage $homePage `
+ -ReplyUrls $homePage `
+ -IdentifierUris $appIdURI `
+ -LogoutUrl $logoutURI `
+ -RequiredResourceAccess $requiredResourcesAccess `
+ -PasswordCredentials $appKey `
+ -AvailableToOtherTenants $true
+
+ # Creating the Service Principal for the application
+ $servicePrincipal = New-AzureADServicePrincipal -AppId $aadApplication.AppId
+
+ Write-Host "Assigning Permissions" -ForegroundColor Yellow
+
+ # Assign application permissions to the application
+ foreach ($app in $requiredResourcesAccess) {
+ $reqAppSP = $rsps | Where-Object {$_.appid -contains $app.ResourceAppId}
+ Write-Host "Assigning Application permissions for $($reqAppSP.displayName)" -ForegroundColor DarkYellow
+ foreach ($resource in $app.ResourceAccess) {
+ if ($resource.Type -match "Role") {
+ New-AzureADServiceAppRoleAssignment -ObjectId $serviceprincipal.ObjectId `
+ -PrincipalId $serviceprincipal.ObjectId -ResourceId $reqAppSP.ObjectId -Id $resource.Id
+ }
+ }
+ }
+
+ # This provides the application with access to your customer tenants.
+ $group = Get-AzureADGroup -Filter "displayName eq 'Adminagents'"
+ Add-AzureADGroupMember -ObjectId $group.ObjectId -RefObjectId $servicePrincipal.ObjectId
+
+ Write-Host "App Created" -ForegroundColor Green
+
+ # Define parameters for Microsoft Graph access token retrieval
+ $client_id = $aadApplication.AppId;
+ $client_secret = $appkey.Value
+ $tenant_id = (Get-AzureADTenantDetail).ObjectId
+ $resource = "https://graph.microsoft.com"
+ $authority = "https://login.microsoftonline.com/$tenant_id"
+ $tokenEndpointUri = "$authority/oauth2/token"
+
+ # Get the access token using grant type password for Delegated Permissions or grant type client_credentials for Application Permissions
+
+ $content = "grant_type=client_credentials&client_id=$client_id&client_secret=$client_secret&resource=$resource"
+
+ # Try to execute the API call 6 times
+
+ $Stoploop = $false
+ [int]$Retrycount = "0"
+ do {
+ try {
+ $response = Invoke-RestMethod -Uri $tokenEndpointUri -Body $content -Method Post -UseBasicParsing
+ Write-Host "Retrieved Access Token" -ForegroundColor Green
+ # Assign access token
+ $access_token = $response.access_token
+ $body = $null
+
+ $body = Invoke-RestMethod `
+ -Uri $UriForApplicationPermissionCall `
+ -Headers @{"Authorization" = "Bearer $access_token"} `
+ -ContentType "application/json" `
+ -Method GET `
+
+ Write-Host "Retrieved Graph content" -ForegroundColor Green
+ $Stoploop = $true
+ }
+ catch {
+ if ($Retrycount -gt 5) {
+ Write-Host "Could not get Graph content after 6 retries." -ForegroundColor Red
+ $Stoploop = $true
+ }
+ else {
+ Write-Host "Could not get Graph content. Retrying in 5 seconds..." -ForegroundColor DarkYellow
+ Start-Sleep -Seconds 5
+ $Retrycount ++
+ }
+ }
+ }
+ While ($Stoploop -eq $false)
+
+ $appInfo = [pscustomobject][ordered]@{
+ ApplicationName = $ApplicationName
+ TenantName = $tenantName
+ TenantId = $tenant_id
+ clientId = $client_id
+ clientSecret = $client_secret
+ ApplicationPermissions = $ApplicationPermissions
+ }
+
+ $AppInfo | Export-Csv C:\temp\AzureADApp.csv -Append -NoTypeInformation
+}
+else {
+ Write-Host "Microsoft Graph Service Principal could not be found or created" -ForegroundColor Red
+}
\ No newline at end of file
diff --git a/SyncMicrosoftSecureScoreReports/SyncSecureScoreScript.ps1 b/SyncMicrosoftSecureScoreReports/SyncSecureScoreScript.ps1
new file mode 100644
index 0000000..2ee7cb7
--- /dev/null
+++ b/SyncMicrosoftSecureScoreReports/SyncSecureScoreScript.ps1
@@ -0,0 +1,712 @@
+# Azure AD App Details
+$client_id = "EnterClientIDHere"
+$client_secret = "EnterClientSecretHere="
+$tenant_id = "EnterTenantIDHere"
+$ListName = "Office 365 - IT Glue match register"
+$graphBaseUri = "https://graph.microsoft.com/v1.0/"
+$siteid = "root"
+$TableHeaderColour = "#00a1f1"
+
+# IT Glue Details
+$ITGbaseURI = "https://api.itglue.com"
+$ITGkey = "EnterITGlueIDHere"
+$ITGheaders = @{"x-api-key" = $ITGkey}
+$SecureScoreAssetName = "Microsoft Secure Score"
+
+function New-GCITSSharePointColumn($Name, $Type, $Indexed, $lookupListName, $lookupColumnPrimaryName, $lookupColumnName) {
+
+ $column = [ordered]@{
+ name = $Name
+ indexed = $Indexed
+ $Type = @{}
+ }
+
+ if ($lookupListName -and $type -contains "lookup") {
+ $list = Get-GCITSSharePointList -ListName $lookupListName
+ if ($list) {
+ $column.lookup.listId = $list.id
+ $column.lookup.columnName = $lookupColumnName
+ }
+ }
+ return $column
+}
+
+function New-GCITSSharePointList ($Name, $ColumnCollection) {
+ $list = @{
+ displayName = $Name
+ columns = $columnCollection
+ } | Convertto-json -Depth 10
+
+ $newList = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method POST -Body $list
+ return $newList
+}
+
+
+function New-GCITSSharePointListItem($ItemObject, $ListId) {
+ $itemBody = @{
+ fields = $ItemObject
+ } | ConvertTo-Json -Depth 10
+
+ $listItem = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists/$listId/items" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method Post `
+ -Body $itemBody
+}
+
+function Remove-GCITSITGItem ($Resource,$existingItem){
+ $item = Invoke-RestMethod -Method DELETE -Uri "$ITGbaseURI/$Resource/$($existingItem.id)" -Headers $ITGheaders
+}
+
+function Get-GCITSSharePointListItem($ListId, $ItemId, $Query) {
+
+ if ($ItemId) {
+ $listItem = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items/$ItemId `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = $listItem
+ }
+ elseif ($Query) {
+ $listItems = $null
+ $listItems = Invoke-RestMethod -Uri "$graphBaseUri/sites/$siteid/lists/$listId/items/?expand=fields&`$filter=$Query" `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = @()
+ $value = $listItems.value
+ if ($listitems."@odata.nextLink") {
+ $nextLink = $true
+ }
+ if ($nextLink) {
+ do {
+ $listItems = Invoke-RestMethod -Uri $listitems."@odata.nextLink"`
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value += $listItems.value
+ if (!$listitems."@odata.nextLink") {
+ $nextLink = $false
+ }
+ } until (!$nextLink)
+ }
+ }
+ else {
+ $listItems = $null
+ $listItems = Invoke-RestMethod -Uri $graphBaseUri/sites/$siteid/lists/$listId/items?expand=fields `
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value = @()
+ $value = $listItems.value
+ if ($listitems."@odata.nextLink") {
+ $nextLink = $true
+ }
+ if ($nextLink) {
+ do {
+ $listItems = Invoke-RestMethod -Uri $listitems."@odata.nextLink"`
+ -Method Get -headers $SPHeaders `
+ -ContentType application/json
+ $value += $listItems.value
+ if (!$listitems."@odata.nextLink") {
+ $nextLink = $false
+ }
+ } until (!$nextLink)
+ }
+ }
+ return $value
+}
+
+function Get-GCITSSharePointList($ListName) {
+ $list = Invoke-RestMethod `
+ -Uri "$graphBaseUri/sites/$siteid/lists?expand=columns&`$filter=displayName eq '$ListName'" `
+ -Headers $SPHeaders `
+ -ContentType "application/json" `
+ -Method GET
+ $list = $list.value
+ return $list
+}
+function Get-GCITSAccessToken($appCredential, $tenantId) {
+ $client_id = $appCredential.appID
+ $client_secret = $appCredential.secret
+ $tenant_id = $tenantid
+ $resource = "https://graph.microsoft.com"
+ $authority = "https://login.microsoftonline.com/$tenant_id"
+ $tokenEndpointUri = "$authority/oauth2/token"
+ $content = "grant_type=client_credentials&client_id=$client_id&client_secret=$client_secret&username=$UserForDelegatedPermissions&password=$Password&resource=$resource"
+ $response = Invoke-RestMethod -Uri $tokenEndpointUri -Body $content -Method Post -UseBasicParsing
+ $access_token = $response.access_token
+ return $access_token
+}
+
+function Get-GCITSMSGraphResource($Resource) {
+ $graphBaseUri = "https://graph.microsoft.com/beta"
+ $values = @()
+ $result = Invoke-RestMethod -Uri "$graphBaseUri/$resource" -Headers $headers
+ if ($result.value) {
+ $values += $result.value
+ if ($result.'@odata.nextLink') {
+ do {
+ $result = Invoke-RestMethod -Uri $result.'@odata.nextLink' -Headers $headers
+ $values += $result.value
+ } while ($result.'@odata.nextLink')
+ }
+ }
+ else {
+ $values = $result
+ }
+ return $values
+}
+
+function New-GCITSITGTableFromArray($Array, $HeaderColour) {
+ # Remove any empty properties from table
+ $properties = $Array | get-member -ErrorAction SilentlyContinue | Where-Object {$_.memberType -contains "NoteProperty"}
+ foreach ($property in $properties) {
+ try {
+ $members = $Array.$($property.name) | Get-Member -ErrorAction Stop
+ }
+ catch {
+ $Array = $Array | Select-Object -Property * -ExcludeProperty $property.name
+ }
+ }
+ $Table = $Array | ConvertTo-Html -Fragment
+ if ($Table[2] -match " |