-
Notifications
You must be signed in to change notification settings - Fork 149
client/eth: Remove non compliant providers. #2102
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
| ALPHA_HTTP_PORT="38556" | ||
| ALPHA_WS_PORT="38557" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Would like to move this to the full nodes, since that is what would be used irl.
dex/testing/eth/create-node.sh
Outdated
| "${NODE_DIR}/${NAME}.log" C-m | ||
| "${NODE_DIR}/geth-ancient --verbosity 5 --vmdebug --http --http.port " \ | ||
| "${HTTP_PORT} --ws --ws.port ${WS_PORT} --ws.api " \ | ||
| "eth --allow-insecure-unlock " \ |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Removed all the modules except eth. This should be all we need. Also "db" was apparently not a module? This was for the light client harness node.
ERROR[02-03|11:23:46.895] Unavailable modules in HTTP API list unavailable=[db] available="[admin debug web3 eth txpool personal clique net les vflux engine]"
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Noticed this too: #2013 (comment)
No clue why it was ever there. Good to have it here too.
However, didn't we still want txpool? Is the idea that we want it to use the dumbed down fallback path? Or that beta is just used for server?
EDIT: oh I still have the txpool fallback for server in this draft PR: d942900fe10e61e674261e066c5da039d77193f6
Will get that out of draft as soon as I've reviewed the ETH swap gasses and run swaps for both ETH and USDC2 on mainnet ethereum.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
However, didn't we still want txpool? Is the idea that we want it to use the dumbed down fallback path? Or that beta is just used for server?
I guess that server operators will use providers, either by choice or because the eth node can not be kept up %100. I also guess that the txpool type operations will not be available for providers. Maybe we can turn txpool on for one and off for the other? So we can use both for testing.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This is the simnet harness, so I mean if you're testing dexc (client, not server) and want to use the beta node? Would that just be pointless and now expected not to work? I'm fine with that, if that's intended.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This is the simnet harness, so I mean if you're testing dexc (client, not server) and want to use the beta node? Would that just be pointless and now expected not to work?
I didn't think the client needed anything but "eth" and only server needed "txpool" (doesn't need now)
I think client is fine with with either "eth" or "eth,txpool"?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Now alpha is eth and beta is eth,txpool
|
Hmm, actually seems bugged. Doesn't seem to be checking unknown providers either. Will figure it out here. Oh, it checks on creations, I guess it also needs to check on reconfigure. Maybe not every start up? |
|
Oh. Sorry about that. You're right
…On Sun, Feb 5, 2023, 8:39 PM JoeGruffins ***@***.***> wrote:
***@***.**** commented on this pull request.
------------------------------
In dex/testing/eth/create-node.sh
<#2102 (comment)>:
> @@ -135,8 +132,10 @@ if [ "${SYNC_MODE}" = "snap" ]; then
tmux send-keys -t "$TMUX_WIN_ID" "${NODES_ROOT}/harness-ctl/${NAME} --nodiscover " \
"--config ${NODE_DIR}/eth.conf --unlock ${CHAIN_ADDRESS} " \
"--password ${GROUP_DIR}/password --light.serve 25 --datadir.ancient " \
- "${NODE_DIR}/geth-ancient --verbosity 5 --vmdebug 2>&1 | tee " \
- "${NODE_DIR}/${NAME}.log" C-m
+ "${NODE_DIR}/geth-ancient --verbosity 5 --vmdebug --http --http.port " \
+ "${HTTP_PORT} --ws --ws.port ${WS_PORT} --ws.api " \
+ "eth --allow-insecure-unlock " \
This is the simnet harness, so I mean if you're testing dexc (client, not
server) and want to use the beta node? Would that just be pointless and now
expected not to work?
I didn't think the client needed anything but "eth" and only server needed
"txpool" (doesn't need now)
I think client is fine with with either "eth" or "eth,txpool"?
—
Reply to this email directly, view it on GitHub
<#2102 (comment)>, or
unsubscribe
<https://github.com/notifications/unsubscribe-auth/ACHQOSOAWROTGNZABTMUNWLWWBP57ANCNFSM6AAAAAAUP7W3JU>
.
You are receiving this because you commented.Message ID:
***@***.***>
|
8d1cbe9 to
af2eebe
Compare
|
|
||
| if rpc, is := w.node.(*multiRPCClient); is { | ||
| if err := rpc.reconfigure(ctx, cfg.Settings); err != nil { | ||
| walletDir := getWalletDir(w.dir, w.net) |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
The getWalletDir path seems unnecessary. It will end up being something like $HOME/.dexc/simnet/assetdb/eth/simnet and I don't think the last siment is necessary. The keystore folder already lives there though, is it worth changing now?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I've noticed that too. Not sure if we should change it though. However, nobody should be using this on mainnet, and we can move our testnet folders around if we do change it.
Maybe someone else has a more decisive opinion.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This has always bugged me too. On one hand, the asset package shouldn't make assumptions about what the caller is going to give. On the other hand, as you pointed out, it's stupid with the extra directory.
Anyway, won't this change bork existing wallets?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Anyway, won't this change bork existing wallets?
Yes. Existing testnet eth multiprc wallets.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Just leaving for now, can be addressed in another pr if necessary.
af2eebe to
0856e0b
Compare
0856e0b to
fb3e0e3
Compare
|
Just rebased. |
fb3e0e3 to
1fd0935
Compare
 norwnd
left a comment
norwnd
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Minor suggestions, just possible improvements.
client/asset/eth/multirpc.go
Outdated
| } | ||
| }() | ||
| if len(providers) != len(unknownEndpoints) { | ||
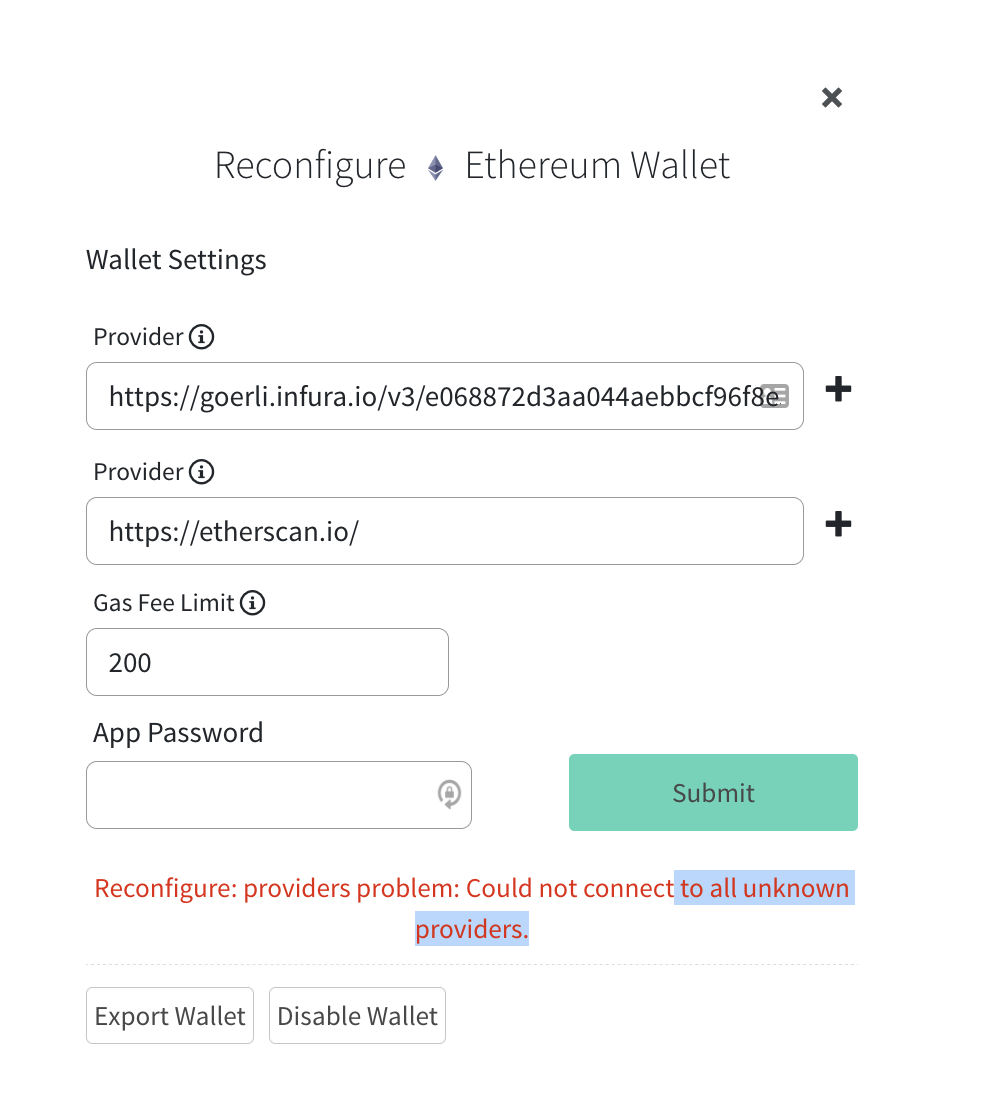
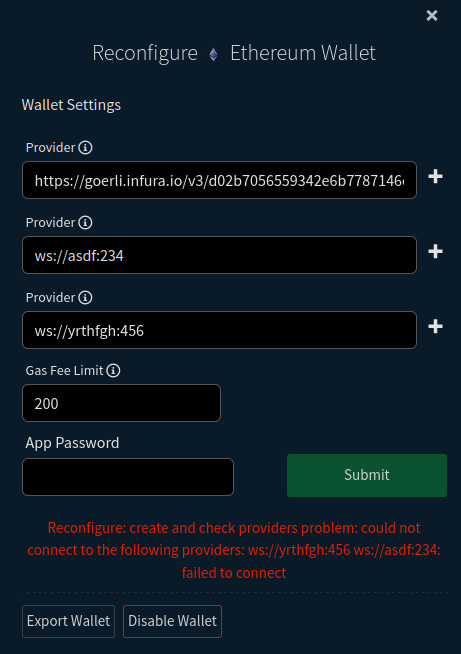
| return errors.New("Could not connect to all unknown providers.") |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
There are logs in the connectProviders function, but yeah, they don't currently make it to the UI.
It's not possible for assets to send UI notifications right? Only core?
Is it easiest to stick the failed providers in that error?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Is it easiest to stick the failed providers in that error?
As a user, by looking at that error in UI I'd want to know which providers I should remove/adjust. Might be easier to "fail fast" and show only one bad provider at a time, so user can repeat adjusting until all supplied configuration is acceptable.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Sticking the failing provider addresses in the error.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| if err := os.WriteFile(path, b, 0644); err != nil { | ||
| log.Errorf("Failed to write compliant providers file: %v", err) | ||
| } |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Maybe return error here instead of just logging it ? So the user can retry saving his configuration (in case it's temporary failure), because he'll have to refill it upon restart ... I can't think of a valid use case to log here instead of erroring right away, thougths ?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
He won't need to refill it, the providers are saved somewhere else. This file is only for a list of user added providers we didn't know about, like random full nodes. If it fails writing, it would mean the provider needs to be checked again if unknown if doing reconfigure. So, it only saves a little time and not every start up. I can't imagine why this would error here under normal circumstances.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I misunderstood it then, thanks for clarifying.
1fd0935 to
6ff317b
Compare
|
Just rebased. |
6ff317b to
eae7c4f
Compare
|
Put all the failed providers in the error so it makes it to the frontend https://github.com/decred/dcrdex/compare/6ff317b8054100e06e059373e230680ab0979217..eae7c4f018735fd1214eefd814a70655bfc27824 |
eae7c4f to
15c6d1d
Compare
|
Was a hairy rebase. |
15c6d1d to
5bd1190
Compare
|
Removed unneeded timed context. Both |
But you're calling with dcrdex/client/asset/eth/eth.go Line 609 in 5bd1190
Probably OK, but it's not timed on that path. EDIT: Oh, you mean |
|
|
Check all providers that are not known to be good. Check them on reconfigure as well. Also use WebSocket with full nodes rather than the light node.
5bd1190 to
66013a0
Compare
|
Merged, but can you clarify your comment about light node for me? |
Ah srry, this is like twice now. I guess you removed it. |
Uh oh!
There was an error while loading. Please reload this page.